Well from popular request I finally got around to loading this up. I went ahead with my favourite retro emulator, PCem for this, as it can nicely emulate an EGA display, unlike most emulators which do VGA, however when it comes to older versions of Microsoft products they really can detect the difference between EGA and VGA.
So, to start off, I downloaded from the project page, this version of PCem, compiled it, and installed MS-DOS 4.01 , from April of 1989. The Windows 3.0 Debug Release 1.14 itself is dated from February 22nd, 1989. Which I figured is close enough to the time period. I’m using the 486SX2/50 because I’m too impatient for the 386 speeds, but it does work fine on 386 or higher emulators. It does NOT work with any 286 emulation. I’m also using the HIMEM.SYS from MS-DOS 4.01 vs the one with the Windows 3.0 (Alpha? Beta? Technical Preview?) since it is slightly newer.
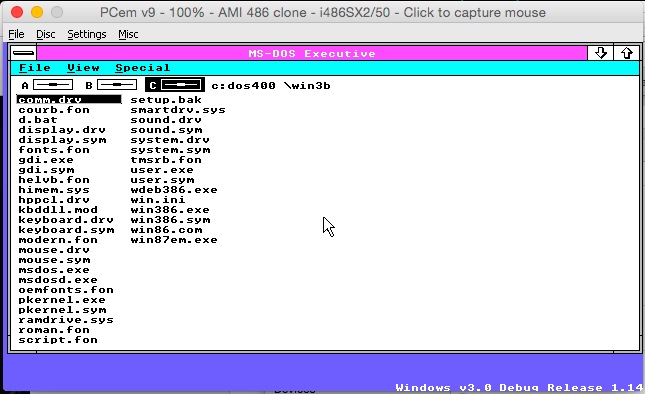
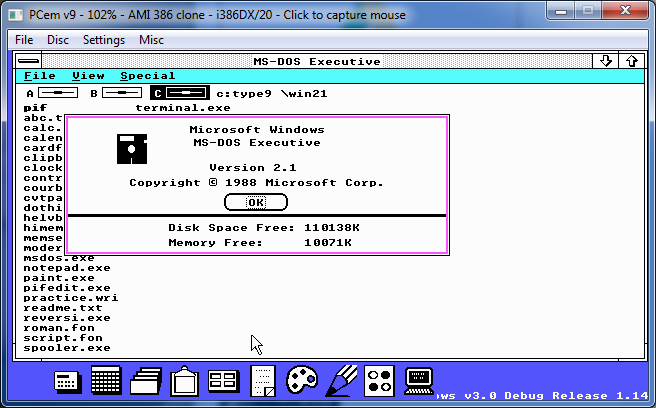
There is no setup program per say, rather it just xcopies all the files to a directory, and from there you run ‘d.bat’ and away you go. This version is hard coded to an EGA display, which again is the reason I went with PCem. Once you start it up, you are greeted with:
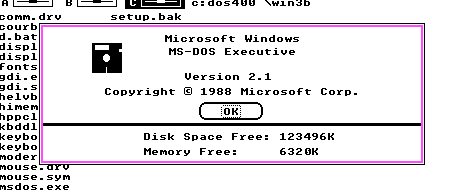
And it identifies itself as Windows Version 2.1
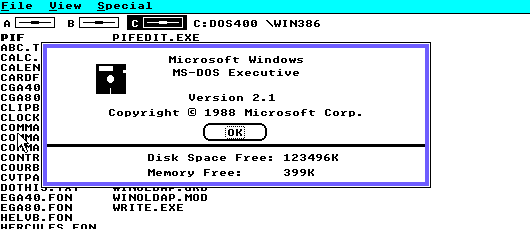
And first thing to notice is that on my setup with 8MB of ram, I have over 6MB of RAM free. Compare this to regular Windows 2.1 which gives me 399Kb of ram in my current setup.
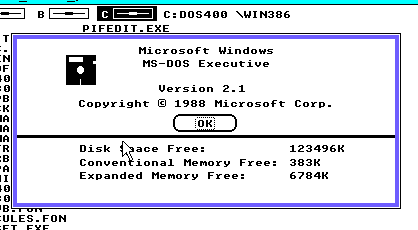
And with Windows/386 Version 2.1 it provides 383Kb of real memory, along with 6.7MB of EMS memory, as the Windows/386 Hypervisor includes EMS emulation.
Of course the major limitation of Windows 2 is that it runs in real mode, or in the case of Windows/386 an 8086VM. As I mentioned a while back in a post about Windows 3.0, This was game changing.
As now with Windows running in protected mode, all the memory in my PC is available to Windows, and I am using MS-DOS, with nothing special.
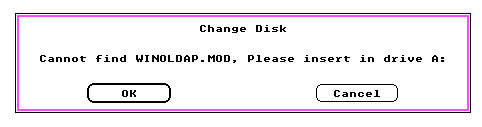
Besides the limitation of being EGA only, the Debug version of 3.0 is that there is no support for MS-DOS applications, as WINOLDAP.MOD is missing.
This is clearly an interim build of Windows 3.0 as mentioned in Murray Sargent’s MSDN blog Saving Windows from the OS/2 Bulldozer. As mentioned from the article they began their work in the summer of 1988, so considering this is early 1989 it shows just how much progress they had made in getting Windows 2 to run in protected mode. Along with Larry Osterman’s MSDN blog post Farewell to one of the great ones, which details how the Windows 3.0 skunkworks project was writing the new improved 386 hypervisor, and how Windows 3.0 got the green light, and changed the direction of not only Microsoft but the entire software industry.
I’ve been able to run most of the Windows 2.1 applets, however I’ve not been able to run Excel 2, or Word 1. I suspect at this point that only small memory model stuff from Windows 1 or 2 is capable of running. Although at the same time, when 3.0 did ship, you really needed updated versions of Word 2 and Excel 3 to operate correctly.
The applets from Windows 2.1 seem to work a LOT better than the one from Windows/386 2.1 if that helps any.
This is an interesting peek at an exceptionally early build of Microsoft Windows.