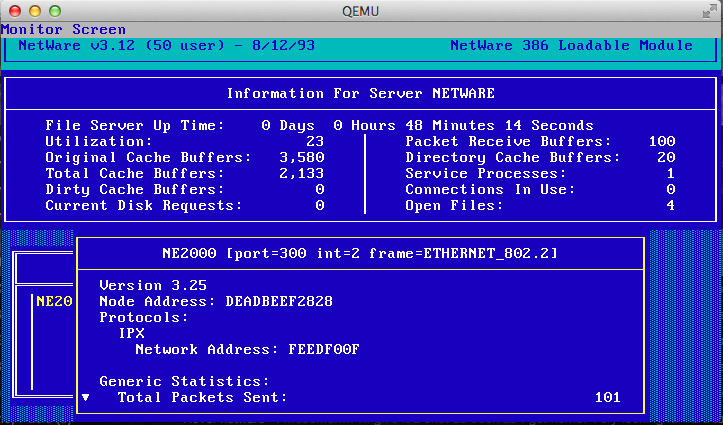
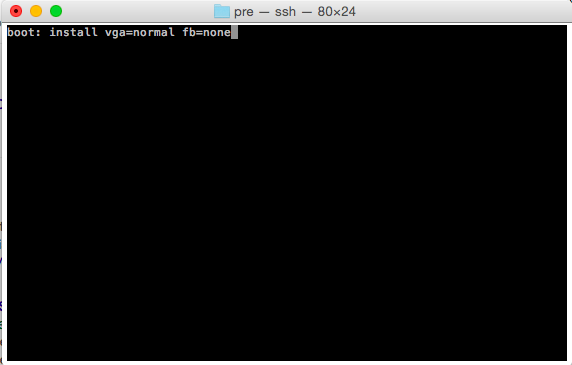
So after nearly 8 years ago from messing around with UnixWare, I wanted to confirm something from a SYSV Unix that has a C compiler that isn’t GCC, and I remembered I have UnixWare 7.1.1 from a long time ago. Anyways I have long since lost the virtual machine I had installed onto, but I still have media and of course the more important licenses.
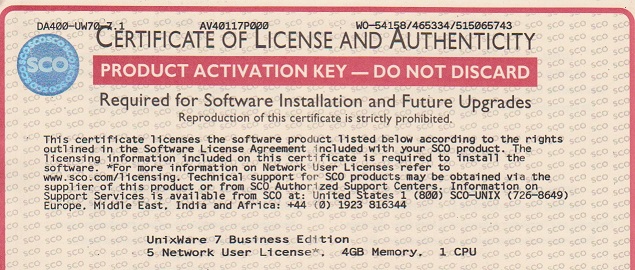
Yep it’s the real thing. So with my certs in hand I do an initial install in Qemu and on reboot the system basically has bricked itself.
WARNING: System is in an unreliable state.
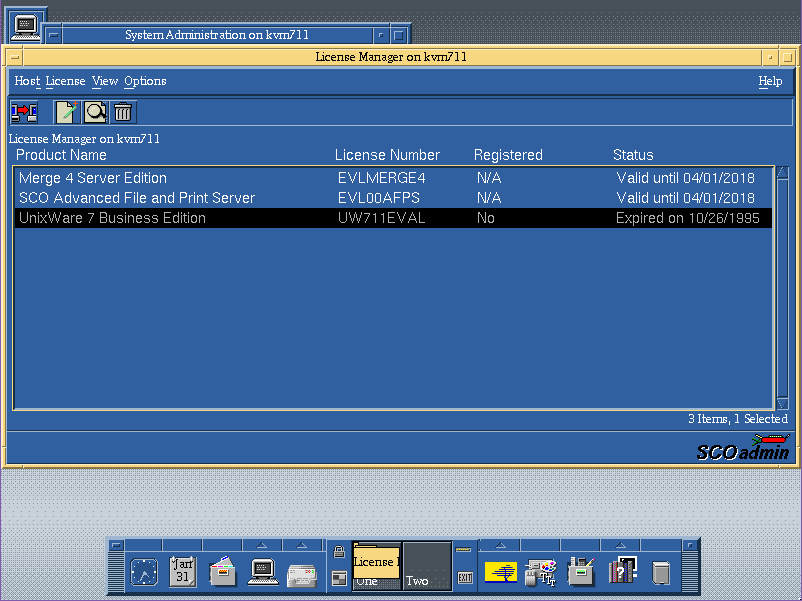
And then looking at the licenses it turns out that my license has expired. What?
Somehow I got lucky before, but it turns out that the installation process for ancient UnixWare is NOT Y2K compliant! And this actually turned out to be a known issue. I can’t find the original article, but a mirror is here: ischo.net
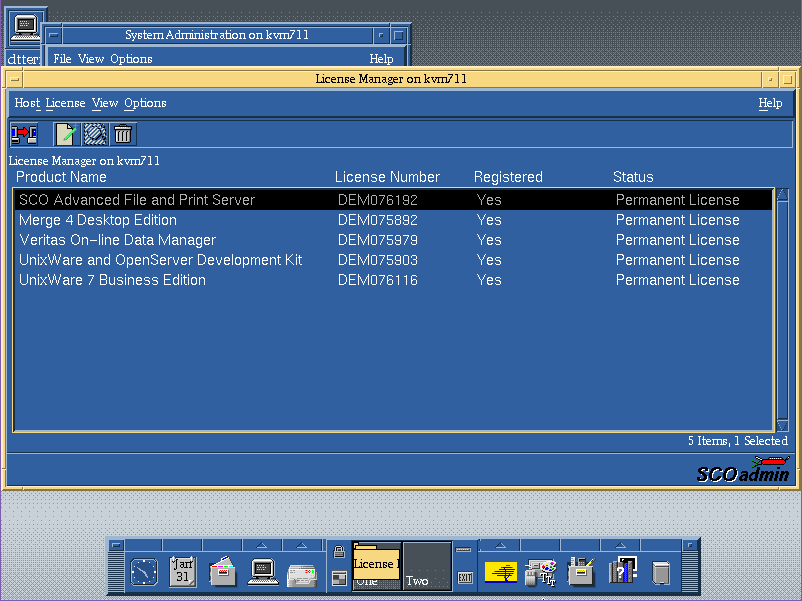
So basically install using an eval license, which will of course expire on install, and then use your actual license after the installation, remove the eval, reboot and all will be well.
License Number: UW711EVAL
License Code: airhorpx
License Data: d60;m7hjbtt
Now isn’t that great.
Although you can’t boot up in any real useful state, the networking will kick people off, and it’ll constantly complain that you are in license violation, you can at least bring up the SCO Admin tool, and add in your actual licenses, and then delete the evals.
Ok, now for the real fun part, flags and how to run with kvm/qemu. Since I was loading this onto a server for remote access something like this works fine for me as I’m using the VNC remote console.
qemu-system-x86_64 -enable-kvm -m 1024 -smp 4 -hda UnixWare.vmdk -cpu pentium -net none -monitor telnet::444,server,nowait -curses -vnc 10.12.0.1:11 -cdrom iso/SCO_UnixWare711.iso
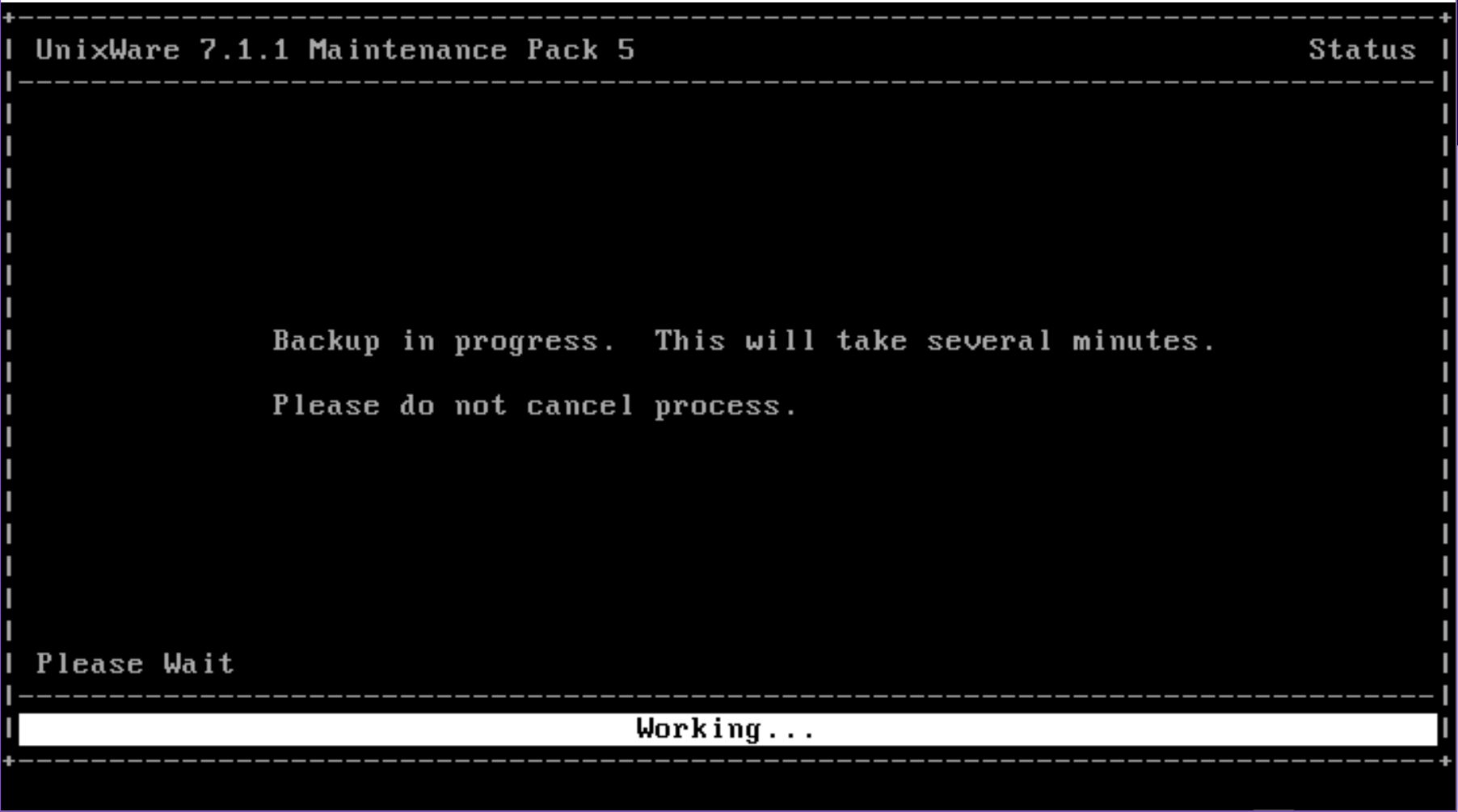
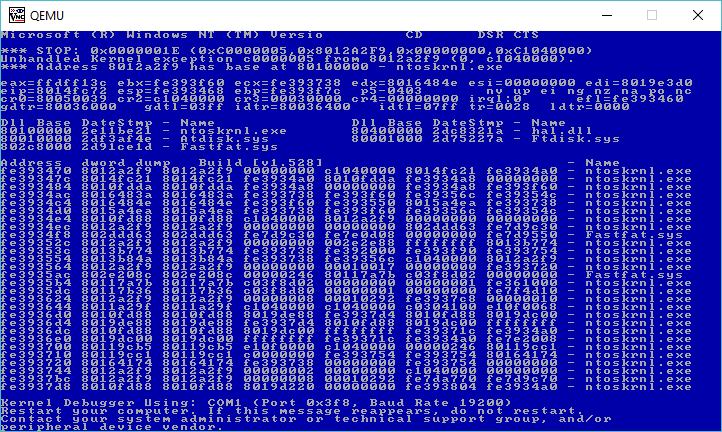
So the key things are to restrict the CPU level, and I’ve deferred the network configuration so I can update network drivers, and the OS. I’ve found that by doing the networking during the install resulted in an OS that crashed with an integer divide by zero after installing the fixpack 5.
Once you have UnixWare 7.1.1 installed, be sure to install Maintenance Pack 5, which is thankfully still online over at sco.com I’d also recommend to do this in single user mode, you can enter single user mode by hitting a key during the boot logo and typing in:
INITSTATE=S
boot
And you’ll boot in single user mode, and can install the Maintenance pack with ease. Until the maintenance pack is installed, expect poor stability, and the system won’t actually listen to the real time clock device, and it’ll accelerate the clock like crazy where I was passing an hour every minute or two.
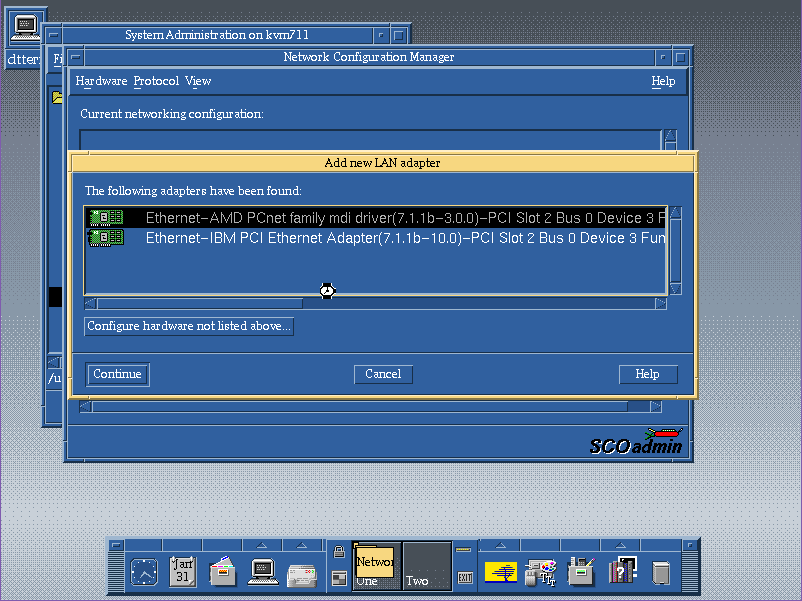
Once the install and update is done, I just added a PCI network card (So older versions of Qemu work well with the ne2k_isa, but newer work much better with the AMD PCNet card.), which is a popular choice for both machines and VM’s of the era. Although you can use SLiRP the built in NAT for Qemu/KVM alternatively you can also use tun/tap. I tried to enable SMP, however it has issues binding to the other processors, although it does see them. And this is better to give full access to the network stack for fun things like FTP, NFS and whatnot.
qemu-system-x86_64 -enable-kvm -m 1024 -smp 4 -hda UnixWare.vmdk -cpu pentium -monitor telnet::444,server,nowait -curses -vnc 10.12.0.1:11 -device pcnet,netdev=net0 -netdev tap,id=net0,ifname=tap10,script=/etc/qemu-ifup
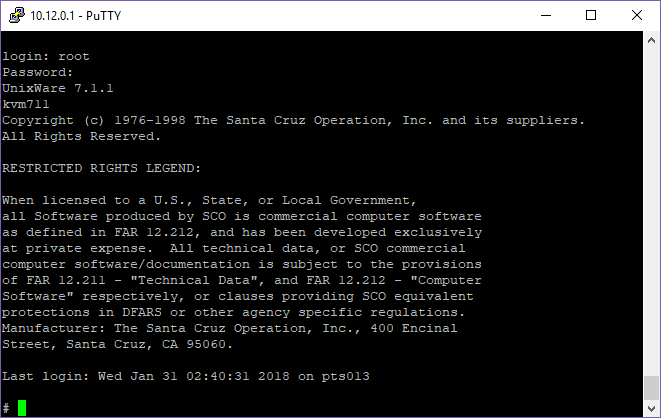
And just like that I can now access the VM.
And for fun…
# uname -a
UnixWare kvm711 5 7.1.1 i386 x86at SCO UNIX_SVR5
# uname -f
architecture=IA32
bus_types=PCI2.10,ISA,PnP1.0
hostname=kvm711.joes.local
hw_provider=Generic AT
hw_serial=DEM076116
kernel_stamp=04/11/11
machine=Pentium
num_cg=1
num_cpu=1
os_base=UNIX_SVR5
os_provider=SCO
release=5
srpc_domain=
sysname=UnixWare
user_limit=5
version=7.1.1
Oh yeah so I don’t forget years from now I’m using the following OS & Qemu version:
# qemu-system-x86_64 -version
QEMU emulator version 2.8.1(Debian 1:2.8+dfsg-6+deb9u3)
# cat /etc/issue
Debian GNU/Linux 9 \n \l
Also I found an eval serial for SMP, but it doesn’t recognize the second processor after the boot.
# psrinfo -v
Status of processor 0 as of 01/31/18 16:40:07
Processor has been on-line since 01/31/18 16:13:57.
The Pentium processor has a i387 floating point processor.
The following conditions exist:
Device drivers are bound to this processor.
I’ll try apparently this as for some reason it doesn’t detect the MP in Qemu/KVM so it never installed the osmp driver.
pkgadd -d cdrom1 osmp
Add the following line to the file /stand/boot:
ACPI=Y






![KVM internal error. Suberror: 1 emulation failure EAX=00000720 EBX=00000050 ECX=fee10050 EDX=00400780 ESI=d02f004c EDI=ff3f0000 EBP=00000d88 ESP=00000d72 EIP=00006725 EFL=00013202 [-------] CPL=3 II=0 A20=1 SMM=0 HLT=0 ES =0047 00080000 00000f9f 0010f300 DPL=3 DS16 [-WA] CS =d517 1aa20000 0000672d 0000ff00 DPL=3 CS16 [CRA] SS =0017 00020000 00000fff 0000f300 DPL=3 DS16 [-WA] DS =bfcf 17f90000 0000033d 0000f300 DPL=3 DS16 [-WA] FS =0000 00000000 ffffffff 00000000 GS =bfff 17ff0000 00000fff 0000f300 DPL=3 DS16 [-WA] LDT=0028 7be57000 0000ffff 00008200 DPL=0 LDT TR =0010 ffe1f6e7 00000067 00008b00 DPL=0 TSS32-busy GDT= 7c7e5000 00001fff IDT= ffe201e0 000003ff CR0=8001001b CR2=00080000 CR3=001b3000 CR4=00000000 DR0=0000000000000000 DR1=0000000000000000 DR2=0000000000000000 DR3=0000000000000000 DR6=00000000ffff0ff0 DR7=0000000000000400 EFER=0000000000000000 Code=ca 76 0f 8b ca eb 0b 03 7e 22 8b ca 3b cb 76 02 8b cb 2b d1 <f3> ab 0b d2 75 ed 2b c0 c3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00](https://virtuallyfun.com/wp-content/uploads/2014/10/KVM-OS2-crash.png)