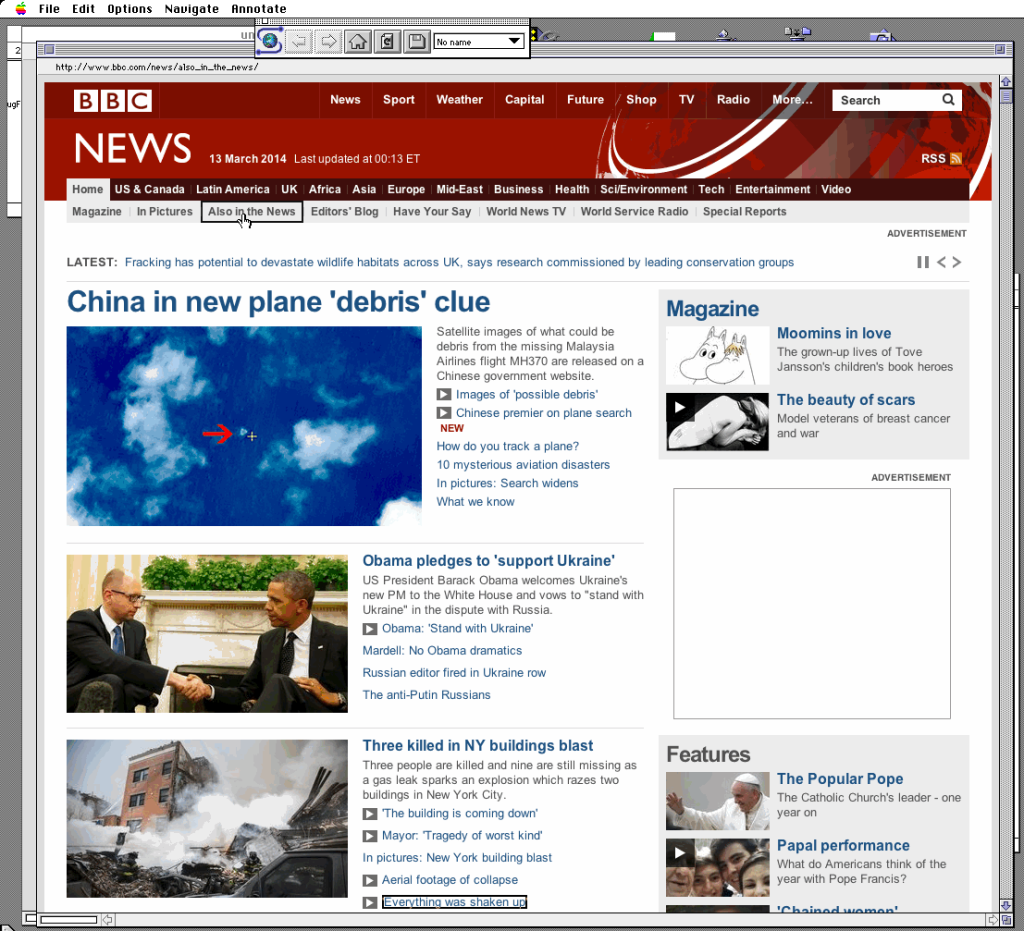
So earlier, I had touched on Minecraft, and lamented on how it doesn’t compress its network data very well. Well, it turns out that yes, in the server.properties file, there is an option network-compression-threshold, which by default is set to 256, meaning packets larger than 256bytes are compressed
network-compression-threshold=256
Using this quick stunnel guide, I thought I’d try a quick experiment. So, I loaded up Titan City, and ran some connection experiments:
First, the Minecraft server with a setting of 256000000 which I would imagine effectively turns off compression. I’m capturing one minutes worth of game play as it tries to render the spawn point. Then again with the threshold set to 256:
12M 28 Apr 13:44 minecraft-nocompression.cap
1.6M 28 Apr 13:46 minecraft-256compression.cap
So, uncompressed it’s 12MB worth of data! While with the Minecraft compression on, it’s 1.6 MB worth of data.
And now with stunnel using zlib compression, we get the following results:
2.1M 28 Apr 13:42 stunnel-nocompressioninserver.cap
1.5M 28 Apr 13:48 stunnel-256compression.cap
2.1MB worth of traffic relying on zlib in this case to do all the compression, and 1.5MB with zlib compressing the Minecraft compression. And for the heck of it, why not compress the data again?
964K 28 Apr 13:46 minecraft-256compression.cap.gz
993K 28 Apr 13:44 minecraft-nocompression.cap.gz
938K 28 Apr 13:48 stunnel-256compression.cap.gz
1.5M 28 Apr 13:42 stunnel-nocompressioninserver.cap.gz
Well, now that is strange, why is the stunnel traffic even compressible, after it’s been encrypted? Kind of weird to me. At any rate, here is some more data thanks to the capinfos program:
# capinfos *cap
File name: minecraft-nocompression.cap
File type: Wireshark/tcpdump/… – pcap
File encapsulation: Ethernet
Packet size limit: file hdr: 1520 bytes
Number of packets: 14 k
File size: 12 MB
Data size: 12 MB
Capture duration: 59 seconds
Start time: Tue Apr 28 13:43:30 2015
End time: Tue Apr 28 13:44:29 2015
Data byte rate: 211 kBps
Data bit rate: 1,689 kbps
Average packet size: 844.05 bytes
Average packet rate: 250 packets/sec
SHA1: ffb5542c47da69ddc93da902136e1173d76b56e0
RIPEMD160: bc2102185a924096a8cf145c54375a05ab90e3c6
MD5: ba0e1addfcb36e7db6314764941fa6af
Strict time order: True
File name: minecraft-256compression.cap
File type: Wireshark/tcpdump/… – pcap
File encapsulation: Ethernet
Packet size limit: file hdr: 1520 bytes
Number of packets: 10 k
File size: 1,686 kB
Data size: 1,524 kB
Capture duration: 54 seconds
Start time: Tue Apr 28 13:45:28 2015
End time: Tue Apr 28 13:46:22 2015
Data byte rate: 28 kBps
Data bit rate: 226 kbps
Average packet size: 150.91 bytes
Average packet rate: 187 packets/sec
SHA1: 5b5e51f53f0716fd84a39120afd68eadbfaf9816
RIPEMD160: f2bf3839c084b1d7b31fce0a8a8ce959316643a7
MD5: dc6f56a5a1c10e642548e0eeb979629b
Strict time order: True
And now let’s look at the stunnel captures:
File name: stunnel-nocompressioninserver.cap
File type: Wireshark/tcpdump/… – pcap
File encapsulation: Ethernet
Packet size limit: file hdr: 1520 bytes
Number of packets: 9,949
File size: 2,159 kB
Data size: 1,999 kB
Capture duration: 59 seconds
Start time: Tue Apr 28 13:41:13 2015
End time: Tue Apr 28 13:42:12 2015
Data byte rate: 33 kBps
Data bit rate: 270 kbps
Average packet size: 201.02 bytes
Average packet rate: 168 packets/sec
SHA1: 418cc249c3393d85e6e59a6e02c02060b7b7ce4f
RIPEMD160: bf7f56af412734260e0e96d1a0c7d2f28be3ba95
MD5: 1b96fce1db9d38d8dbbecf9bb2278079
Strict time order: True
File name: stunnel-256compression.cap
File type: Wireshark/tcpdump/… – pcap
File encapsulation: Ethernet
Packet size limit: file hdr: 1520 bytes
Number of packets: 9,585
File size: 1,554 kB
Data size: 1,401 kB
Capture duration: 59 seconds
Start time: Tue Apr 28 13:47:35 2015
End time: Tue Apr 28 13:48:34 2015
Data byte rate: 23 kBps
Data bit rate: 189 kbps
Average packet size: 146.21 bytes
Average packet rate: 162 packets/sec
SHA1: 19b2bbfff8cd9c5c0e460d64ad0f4b966cf3a141
RIPEMD160: e31c226101daea9327a8b13a4a1012a24bea11c1
MD5: a7b4b0d5ecf3e6a472255cff13466b51
Strict time order: True
Well for me this is still interesting. The stunnel connection sent less packets, and smaller. I know that this is horrible to ‘measure’ like this, and yes none of the datasets are the same, making this kind of bogus. However, honestly compressing with stunnel does feel faster.
So, want to try? I guess I can let people try if they want, but you’ll need stunnel. I’ve read horror stories on griefers and I figure if i raise the bar to connect it’ll be somewhat distractionless.
So here is my stunnel.conf I’m using on the client side.
client = yes
compression = zlib
foreground = yes
debug = 6
[minecraft]
accept = 127.0.0.1:25565
connect = virtuallyfun.com:25566
cert = minecraft.pem
And of course, you need my certificate pair, so here is minecraft.pem:
-----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEArvdyw5UGic3wCDowzGM/ZVdaCrnDFeo8SmkP1jJGIhsAzzMV +56Ctd98raKPnw5nnEtrmV7yImBiF/A32SPbYF6nqBhNKPbrUg4u4dsr9uyo7/F4 00VMcXbcgwc+pDOU5uUCg7hZcmCGolVs+7GxC3R1m8SbPZYvlgcHHJXdnEKL8RG8 z54B2L1Ai76CYlD6Q94QnQxiJricy8DJJP6/ZuqkGg01AcoaCaTOa8mvZMLkBFkj Ase0aX0nSDRxNkBBe/hgwkRuFWaMI1iGgTCX9J1rogLg2WfZoGIFtuYp8jnwiNQQ dEM6TTGURm9iqb78pBd6PwWsFBqOa0GLOEzLzwIDAQABAoIBAAz8/373VBnsuLHT qAW0JGOgfWWobov07G7Vp8BN0Rj9Ci1XbH1WQfvAUGAPXjv/dL+MdbtX6f+VShLe 2TZ8S++2dxmqXCf7VHKt7NsFSxk0bkIJmd+NGGSf3zS21/aWgao2O96NU86CzdvF Hab9hNgF2CktCh0jRfsMIIIFugK8amQGxpKrseSXuuyWGHNW2a6TIHBJRD1L2DQA GMVgmpb43aYQHYqeQLmgP40PkJgByazQRV40zqsap1DBxNi2TnDjLUWufKACDM64 RPltM8lZm3H2yqVQEQ2yGbzoEuwVysG5+AlDOCVcbDtQqcj5sV/gzL8X+e6DgV+0 o46pZgkCgYEA5QGN+73cApm1OkjsV1OW7RR22EmGWT9HeFFGReWSBsVoDh/dFjIJ /KtE7PbafvMcV8JMTzbSxBElc+nPFsRk8J4W+JD3Bluw0MfU1K+AUEmPsj5bX6O6 9Mv8/n8HVhpUusIFvO7K7HutdxxNOis510AtRL8oA6NFkiUBot5KGUMCgYEAw5c1 UVT+N9nciFKopgJlzfcb60SKy60vtWd3eQOuLuRd+1QhF3VpUzTAvwbLARuYdlYM gIaKcOb7A2+ZNKNCccwP6lTIDEwQuQ3lDyG3KXzHfHocZV4n5uT2SpKLv5NzZlF5 4ealpD5pPwN2c4zpvRDeweWznNahUVngYxma5IUCgYEAvac68eg7g3/OYZWw/WVB kdgn0FmbxN+uDcupWguUkrz7vu7OhyorsTAZ5fFN5GLr7xX/Yn7xr+TPUp6onZ9K RSd3uKU9nutilJVaAkXSCyvQsHoJ7DvJgiBJxm5nIfyufPhgDibosU5/yywKHQld XpFMrClvNwwJes3g/AQB88cCgYEAvOfQ7jG5qrW3Ys765gOQ0gHlrDAyIY+ucXVy FaYxWEbmYnSZ1W9n/54GvzlPXk2JzllDj+rh0TO1olbp0MYRyZj+kiO6Zu4chK7f 2eKFZgOHJDlILbtnrIDdQ58QbEJ8hYkRv9Yli2FgAyVUBTxHEH03uGwjMsq1Wb4F k5FKYYUCgYBSe0wqziRUNjxhig/3g5qG6iGt0jnbHN5eTsNiEqe3QxDLKNERGTS4 pjpS0LV52bEdpX7imsIskmt81ed/cPUEKd6nbYyrLT67fUCeLuQ07Zlebc/PI8AD ZoRiyx8x8k55z143XCIdzIyZTriQ5SkUV33wbzPRF8upD0xaygf2Tw== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIEOTCCAyGgAwIBAgIJAIOpvPCh+v5fMA0GCSqGSIb3DQEBBQUAMIGyMQswCQYD VQQGEwJVUzERMA8GA1UECAwISWxsaW5vaXMxEDAOBgNVBAcMB0NoaWNhZ28xHDAa BgNVBAoME1N1cGVyZ2xvYmFsbWVnYWNvcnAxFjAUBgNVBAsMDVZpcnR1YWxseSBG dW4xGTAXBgNVBAMMEHZpcnR1YWxseWZ1bi5jb20xLTArBgkqhkiG9w0BCQEWHmpz dGV2ZUBzdXBlcmdsb2JhbG1lZ2Fjb3JwLmNvbTAeFw0xNTA0MjgwMjU1MzJaFw0y MDEyMDUwMjU1MzJaMIGyMQswCQYDVQQGEwJVUzERMA8GA1UECAwISWxsaW5vaXMx EDAOBgNVBAcMB0NoaWNhZ28xHDAaBgNVBAoME1N1cGVyZ2xvYmFsbWVnYWNvcnAx FjAUBgNVBAsMDVZpcnR1YWxseSBGdW4xGTAXBgNVBAMMEHZpcnR1YWxseWZ1bi5j b20xLTArBgkqhkiG9w0BCQEWHmpzdGV2ZUBzdXBlcmdsb2JhbG1lZ2Fjb3JwLmNv bTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAK73csOVBonN8Ag6MMxj P2VXWgq5wxXqPEppD9YyRiIbAM8zFfuegrXffK2ij58OZ5xLa5le8iJgYhfwN9kj 22Bep6gYTSj261IOLuHbK/bsqO/xeNNFTHF23IMHPqQzlOblAoO4WXJghqJVbPux sQt0dZvEmz2WL5YHBxyV3ZxCi/ERvM+eAdi9QIu+gmJQ+kPeEJ0MYia4nMvAyST+ v2bqpBoNNQHKGgmkzmvJr2TC5ARZIwLHtGl9J0g0cTZAQXv4YMJEbhVmjCNYhoEw l/Sda6IC4Nln2aBiBbbmKfI58IjUEHRDOk0xlEZvYqm+/KQXej8FrBQajmtBizhM y88CAwEAAaNQME4wHQYDVR0OBBYEFJcb/w/SowAjTa/hvtim9oWYSarZMB8GA1Ud IwQYMBaAFJcb/w/SowAjTa/hvtim9oWYSarZMAwGA1UdEwQFMAMBAf8wDQYJKoZI hvcNAQEFBQADggEBAIISqlsBZKh67of21sJhsavDB4T7xrd/qC5zTUeUioScXr+j n2aziysr+HazliIpVNa5QjicYTniG7urAZdL/zhegSyxEq6r1/BVAks0ooYxJT/f G5EIhQurv3wQcGKSEXx6IA7+kheqYX++XcM6lAz5jPPIXsRV4NDsE7T68vVuQrr/ RYMHkbCXMqCbUq8x8k65KNN3EPJ66lH83kXuQJRazeurJmcquhmWqApjkORS17kq +g2xRlnEolvS7umkGz9cbGP7SAWY+ySVIulKSKUKzji8qK8T/hW0dYWUPTZ6+LZx hHnFJXiaGbnd1sEEB6uVV17XipnE15TGJ8NPT2s= -----END CERTIFICATE-----
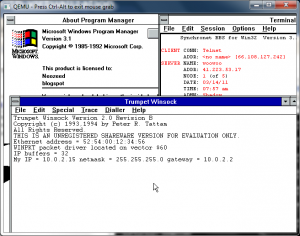
And I run it something like this from the client side…
# stunnel mine.conf
2015.04.28 14:25:23 LOG5[ui]: stunnel 5.16 on x86_64-apple-darwin14.3.0 platform
2015.04.28 14:25:23 LOG5[ui]: Compiled/running with OpenSSL 0.9.8zd 8 Jan 2015
2015.04.28 14:25:23 LOG5[ui]: Threading:PTHREAD Sockets:SELECT,IPv6 TLS:ENGINE,OCSP
2015.04.28 14:25:23 LOG5[ui]: Reading configuration from file mine.conf
2015.04.28 14:25:23 LOG5[ui]: UTF-8 byte order mark not detected
2015.04.28 14:25:23 LOG6[ui]: Compression enabled: 1 method(s)
2015.04.28 14:25:23 LOG6[ui]: Initializing service [minecraft]
2015.04.28 14:25:23 LOG6[ui]: Loading certificate from file: mine.pem
2015.04.28 14:25:23 LOG6[ui]: Loading key from file: mine.pem
2015.04.28 14:25:23 LOG4[ui]: Insecure file permissions on mine.pem
2015.04.28 14:25:23 LOG5[ui]: Configuration successful
Now with stunnel connected, you just have to add a server, but you connect to ‘localhost’. This will have you talking to the stunnel program which then talks to my server, which then redirects to the VM running Minecraft.
No promises on how long it’ll be up though.