So, in my fun and excitement I was putting together a ‘cisco’ network using dynamips that spans a few sites across the world. Â I’m using ancient copies of NT for some servers, although I plan on adding in some 386BSD, SunOS SPARC, and maybe even 68010 based, along with other stuff.
I have the routers running fine, but I felt like adding some kind of external authentication service, and TACACS certainly fits the bill! Â And to be all vintage as usual, I’m not going to use TACACS+ as it’s simply too new, and too big. Â So first things first, I need a copy of the source to TACACS as I’m certainly not going to write my own! Â I found this directory on ftp.funet.fi which has a bunch of old cisco related material, and sure enough there is a tacacsd.c
Even better it’s from 1989 which suits my need for something positively ancient, and simple enough to be a single C file.
/*
* TACACS daemon suitable for using on Un*x systems.
*
* Janruary 1989, Greg Satz
*
* Copyright (c) 1989 by cisco Systems, Inc.
* All rights reserved.
*/
Porting it to run on Winsock, really wasn’t all that hard, I had it running as a standalone program within a few minutes, however there is no password file in NT, so as a simple test, I had simply short circutied the username lookup to always suceeded, along with a password compare.
Since I have VMWare Player installed on my machine, I can use the VMNet 8 connection to talk to my host computer. Â The hard part of course is trying to figure out which NIC is which, but dynamips -e will give you a list like this:
Cisco Router Simulation Platform (version 0.2.16-experimental(merge uppc smips)Build-1-x86/MinGW stable)
Copyright (c) 2005-2011 Christophe Fillot.
Build date: Dec 15 2016 04:20:41
Pcap version [WinPcap version 4.1.3 (packet.dll version 4.1.0.2980), based on libpcap version 1.0 branch 1_0_rel0b (20091008)]
Network device list:
\Device\NPF_{D3DF08C4-7A33-4FE2-9351-000153705A30} : VMware Virtual Ethernet Adapter
\Device\NPF_{3FB194EF-F3A4-45F2-AFAB-A4ABA98E8FF7} : Qualcomm Atheros Ar81xx series PCI-E Ethernet Controller
\Device\NPF_{C46B48B8-74E1-4938-9BFE-E407949A7940} : Microsoft
\Device\NPF_{F72C65CD-C6BC-44FE-9019-C5057DB1D9AB} : VMware Virtual Ethernet Adapter
\Device\NPF_{CE75B9C1-8189-4C8F-8EF6-6CEB0C6D0329} : Microsoft
\Device\NPF_{737A8B62-9A87-4739-9CC2-BF05CDC315D0} : Microsoft
And with that information, we are good to go! Â Since I’m doing a simple test here, I don’t need anything other than a single ethernet to talk to my host, so here is a VERY simple cli to run dynamips:
..\dynamips.exe -P 7200 ..\c7200-is-mz.19991126.bin -t npe-200 -p 0:C7200-IO-FE -s 0:0:gen_eth:\Device\NPF_{D3DF08C4-7A33-4FE2-9351-000153705A30} Â –idle-pc 0x604f1da0 -X
And I’m off booting!
Cisco Router Simulation Platform (version 0.2.16-experimental(merge uppc smips)Build-1-x86/MinGW stable)
Copyright (c) 2005-2011 Christophe Fillot.
Build date: Dec 15 2016 04:20:41
Pcap version [WinPcap version 4.1.3 (packet.dll version 4.1.0.2980), based on libpcap version 1.0 branch 1_0_rel0b (20091008)]
Idle PC set to 0x604f1da0.
IOS image file: ..\c7200-is-mz.19991126.bin
ILT: loaded table "mips64j" from cache.
ILT: loaded table "mips64e" from cache.
ILT: loaded table "ppc32j" from cache.
ILT: loaded table "ppc32e" from cache.
vtty_term_init
CPU0: carved JIT exec zone of 64 Mb into 2048 pages of 32 Kb.
C7200 instance 'default' (id 0):
VM Status : 0
RAM size : 256 Mb
IOMEM size : 0 Mb
NVRAM size : 128 Kb
NPE model : npe-200
Midplane : vxr
IOS image : ..\c7200-is-mz.19991126.bin
Loading ELF file '..\c7200-is-mz.19991126.bin'...
ELF entry point: 0x80008000
C7200 'default': starting simulation (CPU0 PC=0xffffffffbfc00000), JIT enabled.
mips64_test.s ROMMON emulation microcode.
mips64_test.s Launching IOS image at 0x80008000...
Self decompressing the image : ####()## [OK]
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco Internetwork Operating System Software
IOS (tm) 7200 Software (C7200-IS-M), Experimental Version 12.0(20000110:181554) [otroan-thanksgiving-rel 175]
Copyright (c) 1986-2000 by cisco Systems, Inc.
Compiled Thu 20-Jan-00 15:07 by otroan
Image text-base: 0x60008900, data-base: 0x613D0000
cisco 7206VXR (NPE200) processor with 253952K/8192K bytes of memory.
R5000 CPU at 200Mhz, Implementation 35, Rev 1.2
6 slot VXR midplane, Version 2.1
Last reset from power-on
Bridging software.
X.25 software, Version 3.0.0.
1 FastEthernet/IEEE 802.3 interface(s)
125K bytes of non-volatile configuration memory.
4096K bytes of packet SRAM memory.
65536K bytes of ATA PCMCIA card at slot 0 (Sector size 512 bytes).
8192K bytes of Flash internal SIMM (Sector size 256K).
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: no
Press RETURN to get started!
Next I need to take note of how VMWare & Windows have configured my VMNet8 adapter, and configure the router accordingly:
Ethernet adapter VMware Network Adapter VMnet8:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::fcd4:2983:bcba:2d63%19
IPv4 Address. . . . . . . . . . . : 192.168.254.1
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
So Im using 192.168.254.1/24 so let’s setup the router. Â Let’s give it a .10 for the heck of it. Â Also I’m going to turn off DNS name resolution for the moment.
00:00:02: %DEC21140-3-DUPLEX_SPEED: FastEthernet0/0 doesn't support the configured duplexand speed combination
00:00:02: %DEC21140-3-DUPLEX_SPEED: FastEthernet0/0 doesn't support the configured duplexand speed combination
00:00:02: %DEC21140-3-DUPLEX_SPEED: FastEthernet0/0 doesn't support the configured duplexand speed combination
00:00:32: %LINK-5-CHANGED: Interface FastEthernet0/0, changed state to administratively down
00:00:32: %SYS-5-RESTART: System restarted --
Cisco Internetwork Operating Sys
Router>
Router>tem Software
IOS (tm) 7200 Software (C7200-IS-M), Experimental Version 12.0(20000110:181554) [otroan-thanksgiving-rel 175]
Copyright (c) 1986-2000 by cisco Systems, Inc.
Compiled Thu 20-Jan-00 15:07 by otroan
00:00:33: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to down
Router>ena
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int fa0/0
Router(config-if)#ip address 192.168.254.10 255.255.255.0
Router(config-if)#no shut
Router(config-if)#exit
Router(config)#ip route 0.0.0.0 0.0.0.0 192.168.254.1
00:01:29: %DEC21140-3-DUPLEX_SPEED: FastEthernet0/0 doesn't support the configured duplexand speed combination
00:01:31: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
00:01:32: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Router(config)#no ip domain-lookup
Router(config)#exit
Router#wr
Building configuration...
[OK]
Router#
00:01:39: %SYS-5-CONFIG_I: Configured from console by console
And if everything is going well, I can now ping from Windows!
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Users\neozeed>ping 192.168.254.10
Pinging 192.168.254.10 with 32 bytes of data:
Reply from 192.168.254.10: bytes=32 time=54ms TTL=255
Reply from 192.168.254.10: bytes=32 time=31ms TTL=255
Reply from 192.168.254.10: bytes=32 time=31ms TTL=255
Reply from 192.168.254.10: bytes=32 time=31ms TTL=255
Ping statistics for 192.168.254.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 31ms, Maximum = 54ms, Average = 36ms
C:\Users\neozeed>
Awesome! Â Pinging from the cisco however fails.
Router#ping 192.168.254.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.254.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
This fails as Windows by default has it’s firewall on, which then blocks all incoming traffic. However to see that the ICMP would have succeded, you can look at the arp table, and the .1 address should have been learned:
Router#show arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.254.1 0 0050.56c0.0008 ARPA FastEthernet0/0
Internet 192.168.254.10 - ca00.3730.0000 ARPA FastEthernet0/0
We can either diable the firewall, or we can add a rule to permit ICMP. To do either you need to go to the firewall control panel in Windows. Â In this quick example, I’m going to build a rule using the firewall control pannel.
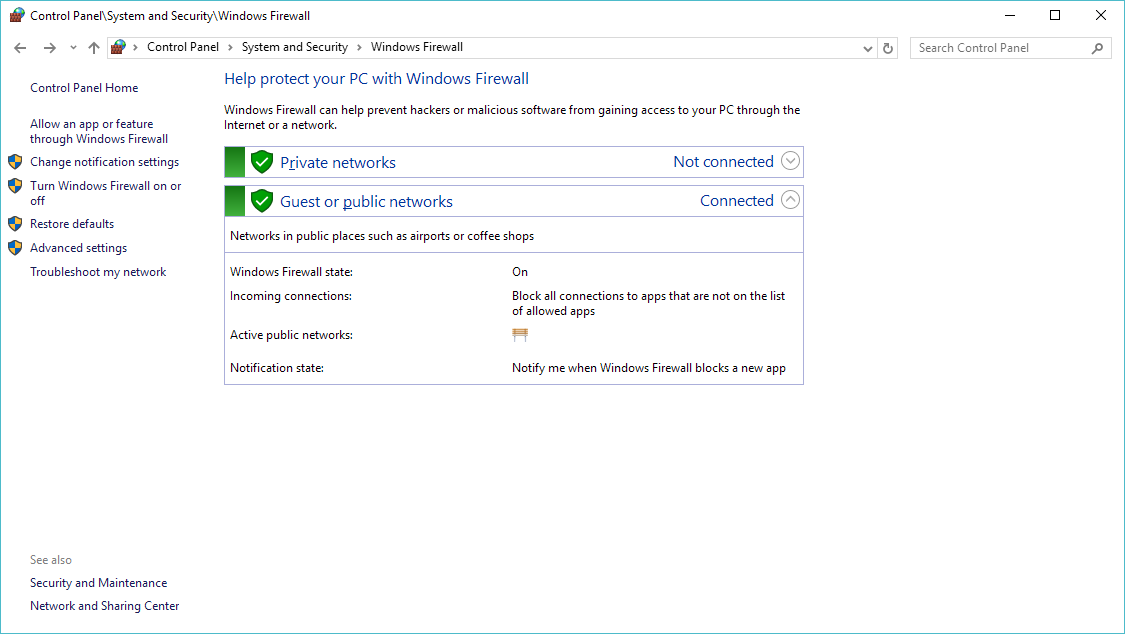
So hit the advanced settings to the left.
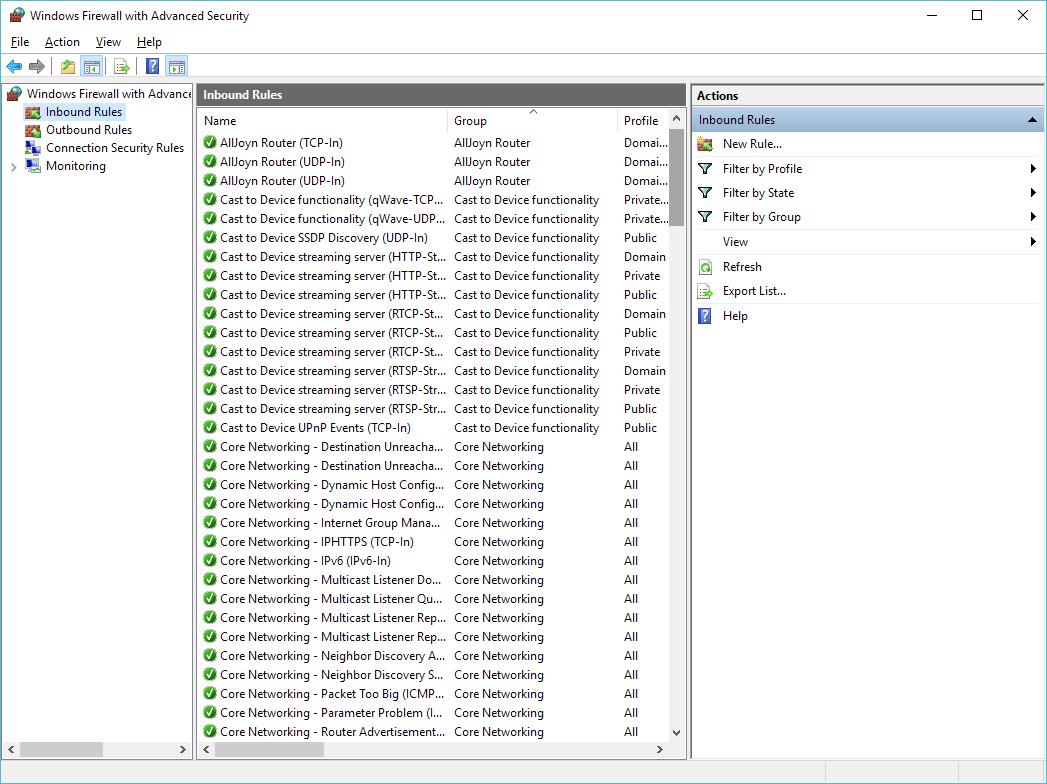
Click on the ‘Inbound Rules’, and now we are going to create a new rule.
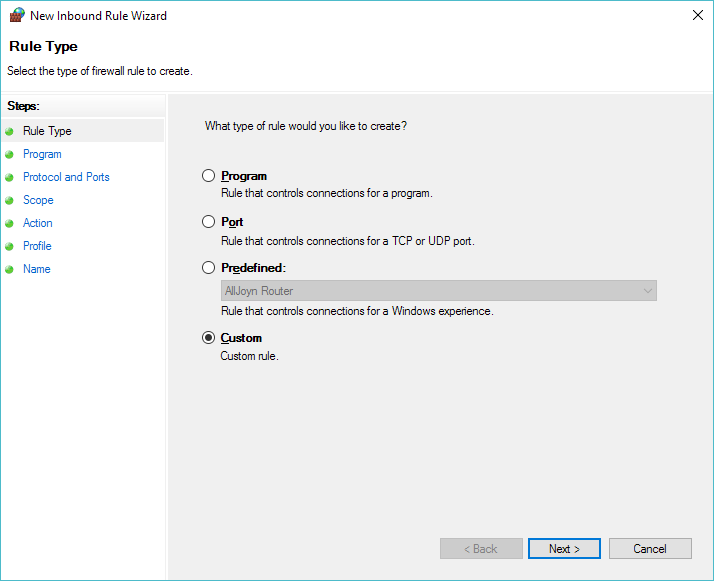
Select a Custom Rule
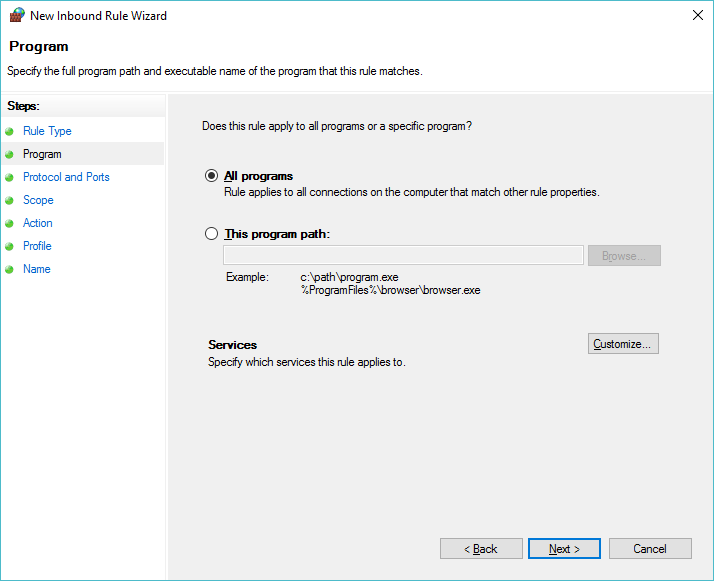
Allow ‘All Programs’
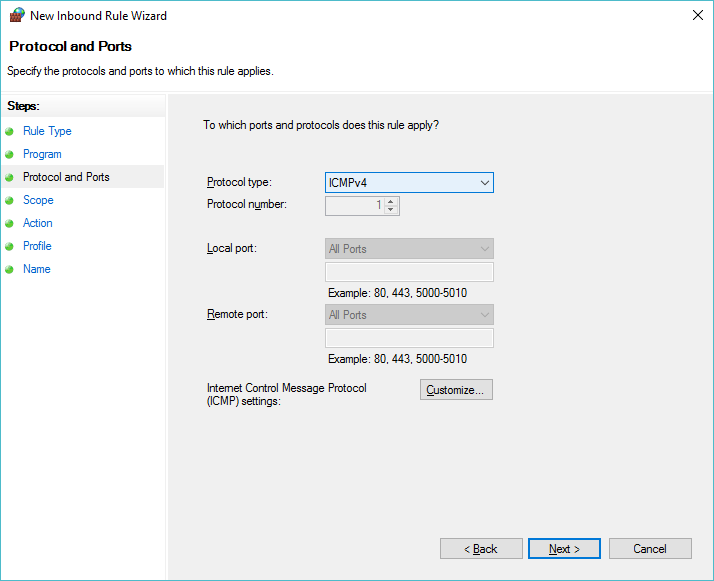
Then set the protocol to ICMPv4
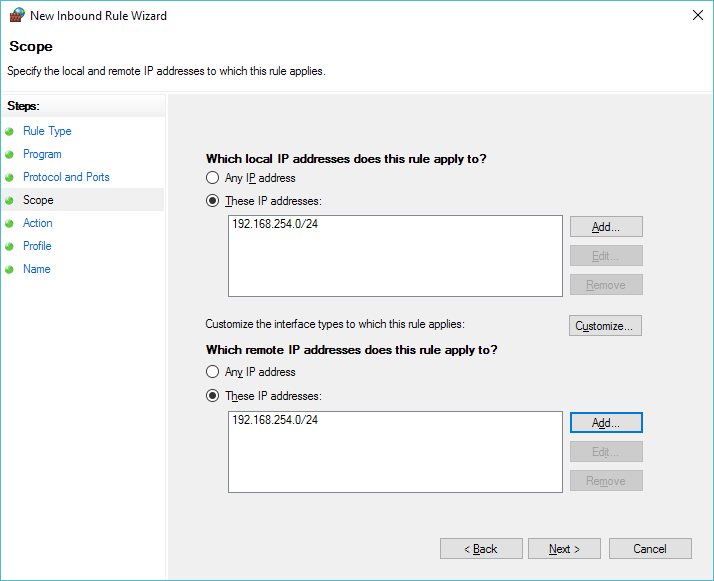
Now we can select the scope of the rule, in this case we are going to allow the 192.168.254.0/24 network to pass icmp traffic to us. Â Add it as a source and destination.
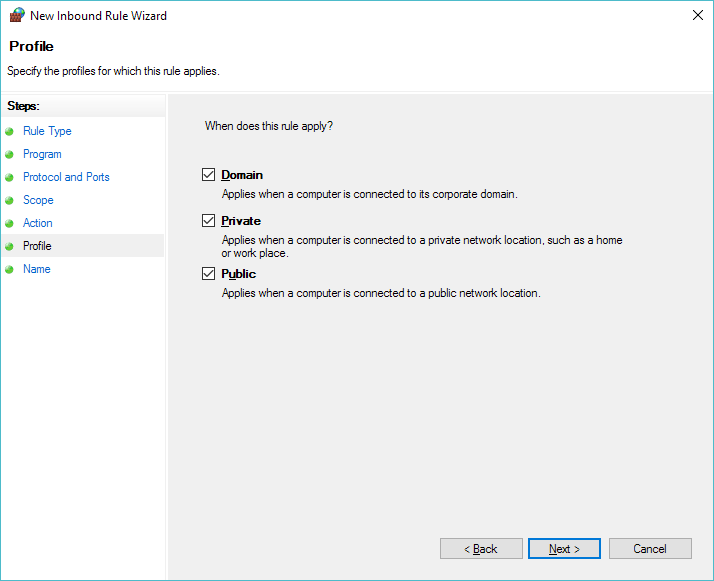
In this quick example I’m applying it everywhere.  I suppose a better  setup would be to make sure the VMNet 8 adapter is a ‘Private’ network, and ONLY apply this to the Private domain.
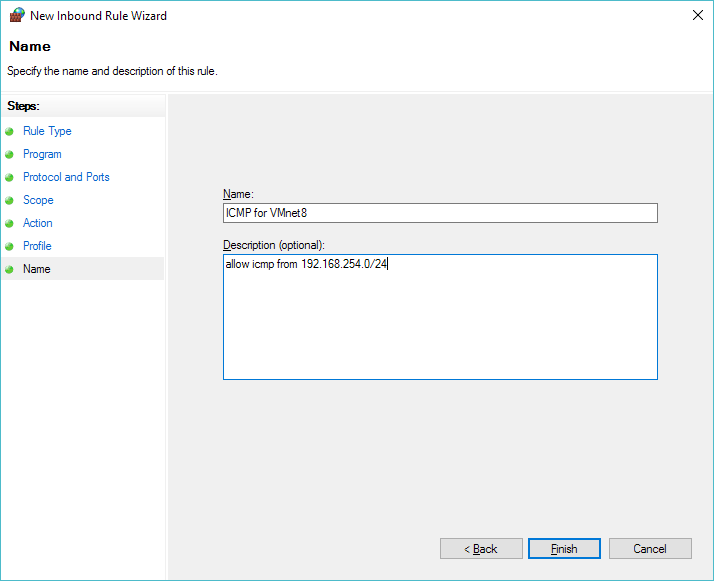
Then give it a name, something like ‘ICMP for VMnet8’
Router#ping 192.168.254.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.254.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/30/36 ms
And now we can ping!
Now for the fun, I go ahead and compile my hacked up tacacsd.c, and run it, and then permit it to run on all networks:
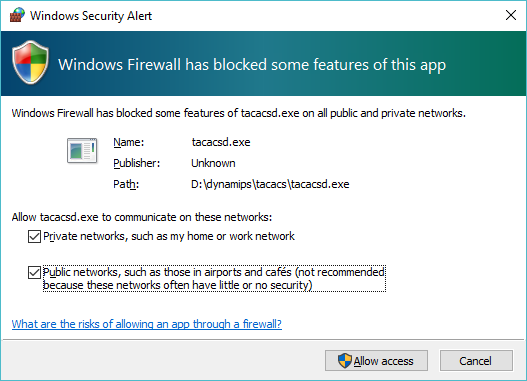
And now I can configure the router to use TACACS. Â Keep in mind, once gain that this is *NOT* TACACS+ so this is done a little differently. Â I’m going to simply set TACACS for telnet connections.
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#tacacs-server host 192.168.254.1
Router(config)#line vty 0 4
Router(config-line)#login tacacs
Router(config-line)#exit
Router(config)#enable password 0 cisco
Router(config)#exit
Router#wr
Building configuration...
[OK]
Router#
00:01:28: %SYS-5-CONFIG_I: Configured from console by console
And now I’m ready to test!
User Access Verification
Username: user
Password:
Router>who
Line User Host(s) Idle Location
0 con 0 idle 00:01:11
* 2 vty 0 user idle 00:00:00 192.168.254.1
Interface User Mode Idle Peer Address
Router>
As you can see I logged in as ‘user’ … and keep in mind my TACACS simply permits anything. As for what tacacsd runs by default:
D:\dynamips\tacacs>tacacsd.exe
server starting
using port 12544
validation request from 192.168.254.10
query for user (pw->pw_gecos) accepted
It’s not exciting, but as you can see it is attempting to look through the gecos to verify the user, but in this case I just allow anything.  And besides just granting anyone the ability to login, let’s take a look on the wire:

WireShark capture of TACACS traffic
As you can see the username & password go over the wire in plain text. Â Even the response is simple enough to decode:
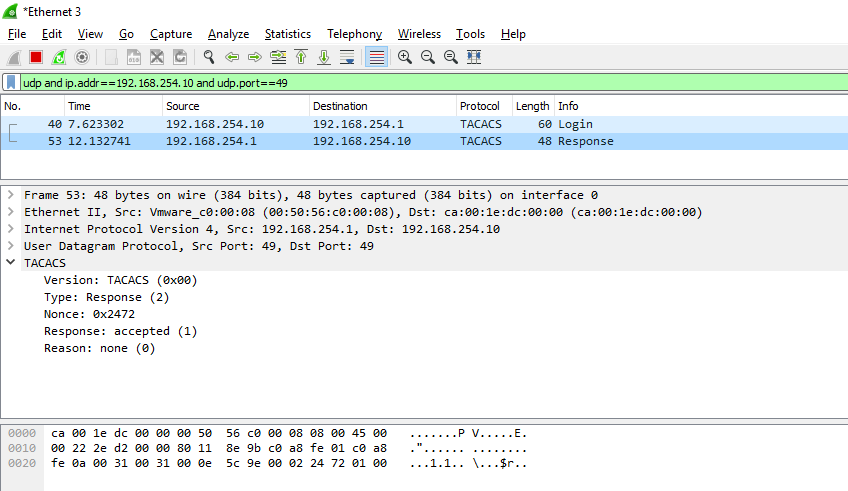
Access granted!
Needless to say this is something that you would NEVER EVER EVER run in a real network.  Of course a system that sits on telnet is vulnerable anyways, but I suppose a TACACS server that lets anyone log in, makes either a VERY trusting network, or a good honeypot.  Against my better judgement, here is tacacsd_win32.c Naturally it could be easily made to verify passwords against pretty much anything.