You too can download it from here:
https://www.microsoft.com/en-ca/software-download/windows11
I for one, blame Canada.
—-edit
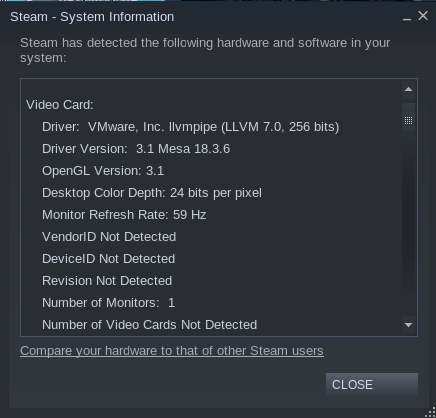
So I installed steam, because why not? But this is steam for Linux. It’s picking up VMware 3D accel.. .I don’t think that’s right. KOTOR2 loads but it’s 100% cpu and 1 frame every 5 seconds.
On the otherhand I’d installed Micropolis ages ago, and it added itself to the 11 launcher:
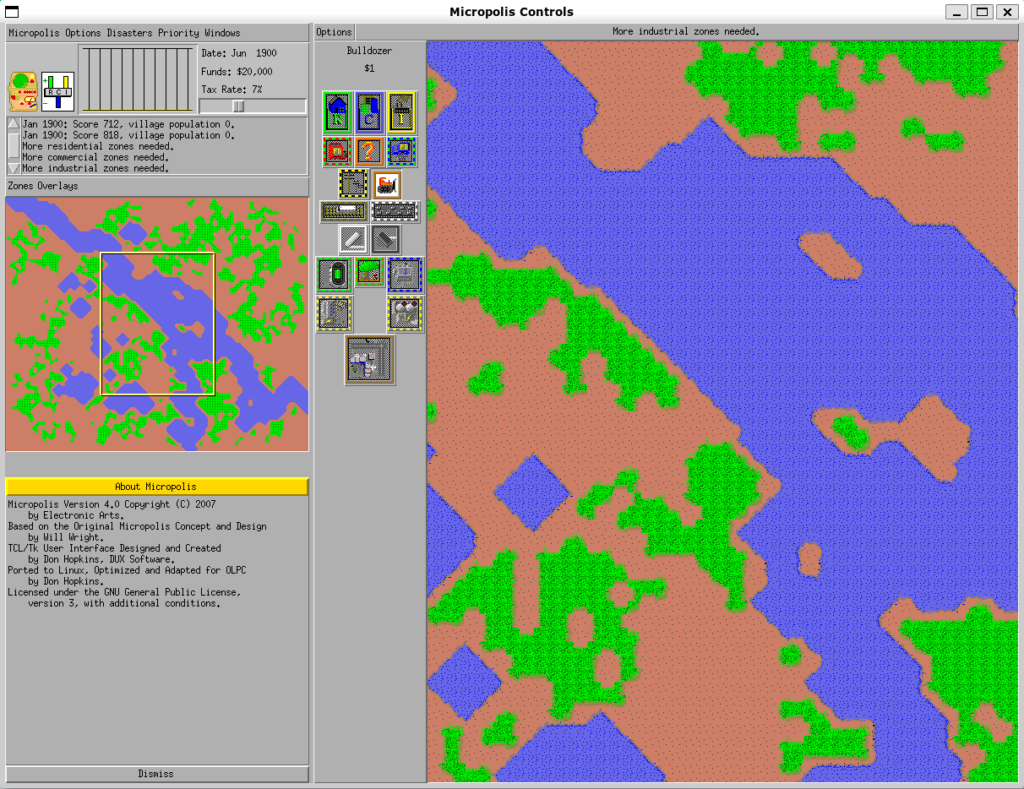
Even better, IT JUST WORKS!

Worth noting that the release version (Win11_English_x64.iso, 5,497,985,024 bytes) won’t install under VirtualBox. Microsoft made a last-minute change to the sysreqs: The installer now requires TPM even for virtual machines, which VBox does not support. The “LabConfig” registry patches that worked in the prerelease versions have no effect.
I’ve only loaded it on my 9th gen i7. I wonder if VMware supports it…?
dism /apply-image /?
Ha 🙂
dism /apply-image, bcdboot, etc indeed works fine under VirtualBox. The Windows 11 guest then boots normally and you can then install the Guest Additions without problems. Tested on a Core i5-4440 host running VirtualBox 6.1.26.
I should mention I did the virtual hard disk partitioning using a Windows 10 ISO, then booted from the Windows 11 ISO to run dism.
Also Windows 11 didn’t complain about booting from an MBR partition table.
VMWare works, but you have to encrypt the VM to add a virtual TPM.
https://eternallybored.org/imgs/compstuff/win11vmware.png
I hate that requirement. Apparently you can patch vmware-vmx.exe to disable that check: https://twitter.com/gentilkiwi/status/1246838943489953793 but I don’t know where exactly to change what. Can anybody figure it out?
Well, they removed that requirement in the just-now released VMware Workstation v16.2.0: https://blogs.vmware.com/workstation/2021/10/workstation-16-2-now-available.html
You do have to edit the .vmx file manually but no biggie. I tested it and W11 installed happily without any other trickery.
Yup, though 16.2.0 seems to have been rushed a bit – the new virtual hardware version is named “Workstation Beta” in the UI, and there are a few other bugs present (if you create a new VM, don’t click “Customize Hardware” in the last step, as it’ll probably crash Workstation).
I’m currently on 16.2.0 build-18760230 … I’ll have to try an 11 in 11…
In less headline grabbing news, there’s also a new SDK, WDK, ADK, EWDK, etc. These contain tools that run on older releases, many of them back to Win7.
They broke the taskbar. I hate combined label-less buttons! With these ultra wide screens, there is more room then ever for taskbar buttons with labels and what do they do? Remove it all!
Yeah, the new taskbar is atrocious. I installed https://startallback.com/ to get the old taskbar back.
and the start menu… you can’t search installed programs.. it’s very annoying. and all my pinned apps are.. unpinned. thanks?
right click task bar for task man? NOPE!
QEMU is also capable, albeit I’m not keeping notes of specific parameters since there are a multitude of things to check for. Just out of my head, you have to configure Linux kvm-intel or kvm-amd Kernel Modules to enable Nested Virtualization (Comes off by default), a version of the UEFI Firmware edk2/OVMF compiled with Secure Boot support, and perhaps telling QEMU to add a TPM module (Don’t know whenever OVMF offers “Firmware TPM” capabilities, in which case it may not matter).
Also, were you EVER interesed in doing PCI Passthrough (Usually in QEMU)? I’m surprised that there are so few posts here about that matter, giving that it is not only useful for modern gaming but also for retro stuff. On some rare occasions I see people using it to wire old PCI Cards with era-accurate Software running in a VM with current generation computers. A recent example is this guy, that got a SCSI PCI Controller, namely an Adaptec AHA-2930CU: https://akuker.github.io/vfio-pci
Other Hardware that already was tested that way includes original PCI Voodoos and some GeForce 6xxx PCIe series for Windows 98 gaming (Albeit that generation is serviced mostly well between PCem, and Voodoo emulation and/or wrappers).
Sounds like the sort of thing that I expect someone here to eventually want to test at some point.
Isn’t because no one wants to try or talk about it. Is because isn’t reliable across compabible VT-d boards… Specially if what you want to bridge PCI cards to VMs (ofc you want, I can’t think why someone would want to bridge a PCIe one for use with win98 for example).
It depends a lot on the firmware, chipset, and for PCI cards, on the PCI bridge capabilities. That’s why for example, @Toble_miner had to change his board bridge to support stuff the revision came with his wasn’t supporting or was bogus. That’s something not supported on all boards, or something everyone can do, by lack of knowledge or tools (aka, soldering station).
Soldering station is a bit… overkill. Most people that I have seen playing with PCIe-to-PCI Bridges were using Risers, so you could test with several different ones in the same system. A few Motherboards also have onboard Bridges and provide PCI Slots out-of-the-box, but these are totally hit or miss (Seems like the case of that guy). Obviously, you will be unable to use a standard closed computer case with Risers, but if you want to check if something works, it is the most flexible way.
I don’t know about the guy you mentioned, but I have been following the topic in VFIO reddit everytime that someone test these niche things. An example is this one: https://www.reddit.com/r/VFIO/comments/d6ef3i/some_interesting_observations_i_had_that_dont/
So yeah, I know this requires A LOT of trial and error before you get a Bridge/card combination that works, since there are still a lot of uncommon quirks on either the Bridge or the PCI Card itself (As if you didn’t had enough quirks on the base platform). But after the thing matures and you have good enough compatibility lists to know what works and what doesn’t, it should become easier.
I never could get pci passthru to work. It seemed like something that was VERY specific to certain boards on certain firmware to only certain cards.
These days, PCI Passthrough tends to work out-of-the-box if using any Intel Skylake, AMD Zen or later platforms, so anything later than 2015-2017 should work. Some platforms are better than others for certain reasons (Main one is support for optional features line PCIe ACS, which gives better IOMMU Groups granularity), but the basics should work on any of those. Older ones are far more pickier (Theorically VT-d is available from late Core 2 Duo/Quad platforms, circa 2008), and seems that you had bad experiences with those already, so void at all cost.
The vast majority of modern users do PCI Passthrough of Video Cards, that have their own multitude of quirks. The two major ones were that you needed to use certain parameters to hide being in a VM from the nVidia Drivers until recently, and there is also the AMD reset bug which makes the GPU usable only a single time per host power cycle and affects several generations, but there are also workarounds for that, too.
I suppose that if you try any modern combination, it should work with not too much effort. Nearly everyone had write a guide about this, each with his own Hardware. After you find what works on yours, you can then use that as a working base to experiment with other Hardware.
If you are interesed in actual results, I convinced a guy from Vogons to try KVM + Passthrough instead of emulation for W98 gaming and he had success with a PCIe GeForce 6600LE: https://www.win-raid.com/t6017f53-Windows-SE-on-Modern-Hardware-5.html#msg105571
Im too old to keep up with code names, but all my lower end stuff is Xeon E5v2 & v3. The only modern machine I have is the 9th gen i7 I run 11 on now, and it’s my daily machine so I can’t take it down for days to mess with stuff. I guess thats the larger issue it only works in very specific settings in very rare configs. I’m sure with the eventual push to 11 for security reasons there will be a massive surge in disposing of pre 7th gen processors. And to be honest its sad as they do work fine for day to day stuff, especially with all the needed spyware for doing business in China, 12+ physical cores helps so much.
Xeon E5 1600/2600v3 (Haswell-E) should work nicely if you pair them with a server/workstation Motherboard, as VT-d tends to work out-of-the-box on those. On consumer Haswell (Core iX 4000 generation), it was hit or miss. For reference, I have a Xeon E3 1200v3 Haswell on a Supermicro Motherboard, which I purchased back in 2013 specifically for this purpose (And is still my main, and only, computer). The v2 I would avoid because the older it is, the more quirks,, albeit chances are that it works there, too.
If that is your available Hardware, at the platform level you should be good to go unless the Motherboard REALLY sucks. Video Card could be complicated, but any recent GeForce/Radeon “mostly” works for as long that you keep in mind what I mentioned previously.
You should manage to get it working, these days it is extremely well documented how to setup PCI Passthrough on most Linux distributions with a variety of supported Hardware. I would like to see what you can do if you add that into your tool arsenal, as it has some interesing retro uses. Thus you’re the type of person that may have the most fun with it. After getting it working, obviously!
Don’t update. Don’t use Win11, use linux.
Don’t fail for the “security” rhetoric.
MS has to be forced to move their current ways.
how is using tpm to enforce only signed code ‘security rhetoric’?
Did you found a way to build the root on your own trust chain by changing the signature on your CPU security processor core and sign your firmware image against it, with your own private keys as phone and other electronic device makers can do (and no, that isn’t TPM certificate attestation)? If no, then the security they are selling to you is duct tape, just rhetoric, and you know is true. Sure it will keep away the unblessed hacker people, but the blessed ones will be able to do whatever they want as soon as your device manufacturer gives them the keys to do so. And you still will be vulnerable to these keys leaking, which has been probed to be possible.
Personally, at least to me, security duct tape (and wslg btw) isn’t worth all the hassles which Win11 want to push to me. And I wrote the message answering to your “And to be honest its sad as they do work fine for day to day stuff”. But in the end ofc is your choice if you want to support them trashing perfectly usable hardware for duct tape security.
I have to deal with ‘normal people’ and in China. I’d trust the manufactures far more than dumb end users, or random 3rd party ‘must have apps’.
it’s hardly duct tape, anything that you are signing on the same machine is already suspect.
At some point you have to know that everything connected to a network is compromised. Ever since PGP went from being a military grades muntions to being free and open, it’s pretty obvious that none of this stuff matters, it’s just a high enough bar to block anyone below the power of state actor.
little late to the party, but llvmpipe is actually software rendering, not VMware emulated graphics.