From the article here, on August 3rd, (aka yesterday) the purge will be complete. Instead of introducing an update to verify SHA-2 into legacy systems, and re-signing old updates, instead MS has taken the path of obsolesce and pulled the downloads instead.
And we’ve been here before.
Microsoft movie maker was a popular download for Windows XP, and MS removed the download, as hosting it was apparently encouraging people to keep on using XP. Naturally this wasn’t taken as a message that people wanted this kind of product, and why fill a void when you can remove a product? So now the majority of downloads that you will find are infected, corrupted and just going to cause further problems.
And here we go again.
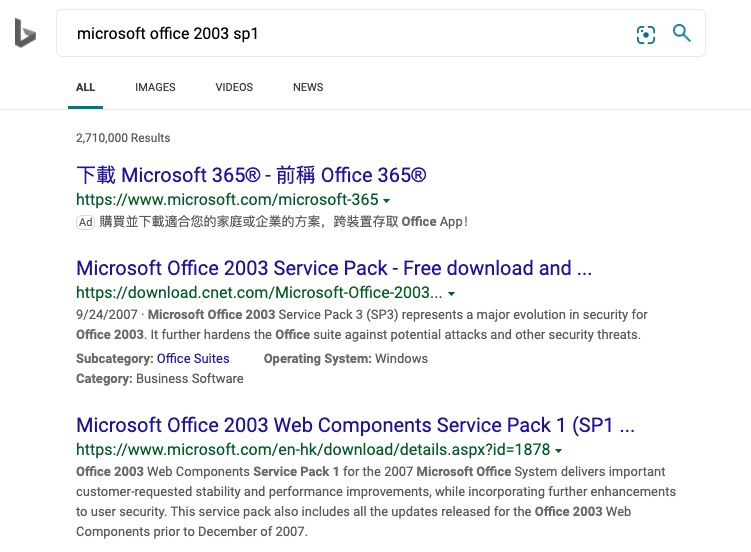
A quick search on BING for MS Office 2003 updates still shows links, but they are simply no more. The purge is in full force, and search pages haven’t caught up. And as you can see cnet is already in the top downloads, and will become the authoritative download by fiat.
Also the early .NET’s deployment packages are no longer for download, while .NET 1.1 SP1 is still online surprisingly. For reference:
$ shasum -a 512256 NDP1.1sp1-KB867460-X86.exe 7b44095feff471dee9366a2153dfe2654d70754c21b7e5204ed950cdf4a3f15a NDP1.1sp1-KB867460-X86.exe
For what it’s worth.
Calculating with shasum offers a few algorighims as this isn’t a simple one shot deal.
-a, --algorithm  1 (default), 224, 256, 384, 512, 512224, 512256
Naturally to add further confusion. Like everything with crypto, it’s so easy to mess it up.
$ shasum -a 1 NDP1.1sp1-KB867460-X86.exe 74a5b25d65a70b8ecd6a9c301a0aea10d8483a23 NDP1.1sp1-KB867460-X86.exe $ shasum -a 224 NDP1.1sp1-KB867460-X86.exe 18507f80722780ca477d7f10528ae28dd176f8d36cbce05a50cc7be0 NDP1.1sp1-KB867460-X86.exe $ shasum -a 256 NDP1.1sp1-KB867460-X86.exe 2c0a35409ff0873cfa28b70b8224e9aca2362241c1f0ed6f622fef8d4722fd9a NDP1.1sp1-KB867460-X86.exe $ shasum -a 384 NDP1.1sp1-KB867460-X86.exe c2372c71f93b5dc2a1c21c804bc74e27d82bfa45ee50fbc9037e713c156f1c591ffbe5e87f94022157906098916403b4 NDP1.1sp1-KB867460-X86.exe $ shasum -a 512 NDP1.1sp1-KB867460-X86.exe bbe643f447f49636732b12d23a052d02681ad41f6920dc1038b073fa600f7589b378ed8e7de97e811543d93ae89ce52871a85ee58aa3b6aeaddc01bc1617ad85 NDP1.1sp1-KB867460-X86.exe $ shasum -a 512224 NDP1.1sp1-KB867460-X86.exe 63b2ffb0c5f1cd68abafba23997482b2087d486dcf60bec6fef7446d NDP1.1sp1-KB867460-X86.exe $ shasum -a 512256 NDP1.1sp1-KB867460-X86.exe 7b44095feff471dee9366a2153dfe2654d70754c21b7e5204ed950cdf4a3f15a NDP1.1sp1-KB867460-X86.exe
Oddly enough a quick search for these checksums isn’t coming up with anything so I guess I’m first. Which of course is a further problem, is that there is no authoritative source from MS. I get the contract obsolescence thing, after-all the strongest competition to NEW MS products is OLD MS products. I still use Excel 3 & MS Word 2, despite having an Office 365 subscription, and various newer versions retail.
The sad thing is that many people will get screwed over from this action, and the only “solution” is of course move to Windows 10, embrace the new, and hope that you don’t have applications that actually require .NET 1.1 (or 1.0!).

“The sad thing is that many people will get screwed over from this action, and the only “solution” is of course move to Windows 10, embrace the new, and hope that you don’t have applications that actually require .NET 1.1 (or 1.0!).”
Or just start backing the opensorce NT alternative: ReactOS :-).
ArchiveTeam have done an emergency grab and uploaded it to archive.org:
https://archive.org/search.php?query=Microsoft+Download+Center&and%5B%5D=collection%3A%22archiveteam%22
Since it was archived as warc.gz, it will be available on the Wayback Machine:
https://web.archive.org/web/*/https://download.microsoft.com/* (really slow to load)
But kb937961 seem to be missing 🙁
I connected an old drive, and I have KB923618.
I guess it’s better than nothing.
Found it on some FTP after searching the file name “owc2007sp1-kb937961-fullfile-en-us.exe” on Google and verified the checksum. A lot of important patches ended up surviving on random servers like this.
https://archive.org/details/owc2007sp1-kb937961-fullfile-en-us
I’ve got a bunch of old Windows, .NET and Office SPs on the server at work, here are my hashes:
“`
16a354a2207c4c8846b617cbc78f7b7c1856340e *.NET 1.1.exe
3dce66bae0dd71284ac7a971baed07030a186918 *dotnetfx35sp1.exe
58da3d74db353aad03588cbb5cea8234166d8b99 *dotNetFx40_Full_x86_x64.exe
f4fc64ebf66978ca95ebf4f5acfd0107d77c5656 *NetFx20SP1_x64.exe
eef5a36924cdf0c02598ccf96aa4f60887a49840 *NetFx20SP1_x86.exe
74a5b25d65a70b8ecd6a9c301a0aea10d8483a23 *NDP1.1sp1-KB867460-X86.exe
535f57e5a8eceab18533c50c0b0e1469ed45331f *NDP1.1sp1-KB886903-X86.exe
dbf23e456103c38626e03720df75c780d9bc48af *NDP1.1sp1-KB953297-X86.exe
a3625c59d7a2995fb60877b5f5324892a1693b2a *.NET 2.0.exe
2c985f3ff1fdccecf89df61918fb55eb4b12edd8 *Exchange 2003 SP2.exe
bb8acbbea695a9579b0b4bca1629cd8a45dbec23 *Exchange 2010 SP2 x64.exe
d939604572d4153dceed78e6b13566af215308f6 *Exchange 2010 SP3 x64.exe
da15b2b0636cb2c9a129a23f90d352db62c059a1 *Office 2000 SP3 EN.exe
ca3ecea811193c889477fa8e2c6c5ba3cd5f075a *Office 2000 SP3 SL.exe
ece919c9b5cad90853261af7093a6432cddc5991 *Office 2000 SR1a EN.exe
09e3185a3ae3d2e241d06905fb03bd06c3a43f07 *Office 2000 SR1a SL.exe
190426eaba1ca82d40ed0e825e98b1263558ef06 *Office 2003 SP2 EN.exe
9b9548a37b471c5dd1368d5b6469ba37bb4b09a7 *Office 2003 SP2 SL.exe
81e8e5b08aa073287ddf5d46b3484e3626659696 *Office 2003 SP3 EN.exe
70dacb63a7fd6e37bf7f12ddc22479e9123dcf82 *Office 2003 SP3 SL.exe
9f3f1fe20261d9c298aec93921c44dc9931dde88 *Office 2007 SP1 En.exe
9e8942c3173c74371a3b84430e0cbea666edb1b4 *Office 2007 SP1 SL.exe
d0ed0f3386d960857e76e89a094b61ceb9811753 *Office 2007 SP2 En.exe
263a23c2367ab73767827ae72e914b342d889756 *Office 2007 SP2 Sl.exe
69a5828265249c9de7f3503102003fe006dc162d *Office 2007 SP3 En.exe
0a707a4962d206aade876403d60ffd70e2297e5c *Office 2007 SP3 Sl.exe
a60e646cdd4761685232bfbabee3b14ee582500e *Office 2010 SP1 En x64.exe
edf28f56a893d4ad92dc359cf029e0e058ea949f *Office 2010 SP1 En x86.exe
8244c2813a882ed97ad51ed6834a2b653a39a5b6 *Office 2010 SP1 Sl x64.exe
30a0e00c348c72e1fad4aa14578a0e6a15af7127 *Office 2010 SP1 Sl x86.exe
3c6ba45d793bcc69dd945c29ce79573415704c75 *Office 2010 SP2 En x64.exe
faa6e4d481e8ae534cbf47afc46c22dc4f43ee3c *Office 2010 SP2 En x86.exe
a001581fb8ff5fd3208e5ff76534cee26ea5d4bd *Office 2010 SP2 SL x64.exe
32d1d880fce5dd191398e9586f834abaa4f7602a *Office 2010 SP2 SL x86.exe
9f6e7b101be5c8a25ba82ccc44ee99a37d55afdc *Office 2013 SP1 En x86.exe
3899b0fd93bfaa21633e64cf937683077368a1e3 *Office 2013 SP1 En.exe
f5379f3b91b90afeb4767772e95657b9c0372f1f *Office 2013 SP1 SL 32.exe
1256c798415d9fb10cae91327cc37fd519b89656 *Office 2013 SP1 Sl.exe
dba8a31687336fcf31570521451a4649d5ec4c07 *Office XP SP3 EN.exe
4f915445a380d9fbff0176f0e9cb761ff33df4d6 *Office XP SP3 SL.exe
69455885be1ae71c115c0a6a5ff072c661685a50 *SQL Server 2000 SP4 x86-KB884525.EXE
737b01db75140dc883714ce06e64e51a37310d34 *SQL Server 2005 SP2 x86-KB921896-ENU.exe
75deaa970beb66df7b41025f7bea9f9cc3b9bb90 *SQL Server 2008 R2 SP2 x64.exe
fadea6d94a014b039839fecc6e6a11c20afa4fa8 *Windows 2000 SP4.exe
f118bd276f4211929719961a2e929b620c1a2234 *Windows 2000 Update Rollup 1.EXE
74865ef2562006e51d7f9333b4a8d45b7a749dab *windows 7 SP1 x64 KB976932.exe
c3516bc5c9e69fee6d9ac4f981f5b95977a8a2fa *windows 7 SP1 x86 KB976932.exe
075e5f909800a210b94033a30993c035a354aa17 *Windows NT4 SP6 (HighEncryption).exe
da4422bfa01f7f62dd4e32f349f1a3cd8db70943 *Windows NT4 SP6-patch (HighEncryption).exe
a99e478222824ea169ba352d50ef37ffef9189a6 *Windows NT4 SP6-patch.exe
1a1c990bcaf9851b8d9e34d2b0cab7814834c837 *Windows NT4 SP6-SYMI (HighEncryption).exe
8caca058c65c73865cdbc3fbee671f41af0bf894 *Windows NT4 SP6-SYMI.exe
a6f920d4d9868cfa8a1c7697813c55d136209664 *Windows NT4 SP6.exe
cdf6552483a5a4491baa195ca76781eeaa059091 *Windows Server 2003 SP1 x86.exe
51e1759a1fda6cd588660324abaed59dd3bbe86b *Windows Server 2003 SP2 x86.exe
7f8e909c52d23ac8b5dbfd73f1f12d3ee0fe794c *Windows Server 2003+XP SP2 x64.exe
908983c5cd8c1112ee452a0a907b546cc70c9d8b *Windows Vista SP1 x64 KB936330.exe
79f3fd5db332b4464d8ebc54da68be8effd760c4 *Windows Vista SP1 x86 KB936330.exe
2eedca0bfa5ae8d1b0acf2117ddc4f15ac5183c9 *Windows Vista+2008 SP2 x64 KB948465.exe
55f17352b4398ecb4f0cc20e3737631420ca1609 *Windows Vista+2008 SP2 x86 KB948465.exe
33a8fef60d48ae1f2c4feea27111af5ceca3c4f6 *Windows XP SP2.exe
36f97f075f2098fe5a0c239cc0b6fded88d5f8aa *Windows XP SP3 Embedded for Point of Service + Fundamentals for Legacy PCs.exe
c81472f7eeea2eca421e116cd4c03e2300ebfde4 *Windows XP SP3.exe
cc2acdd2ef74cbf90896322a2c3d52c8bf908e0c *WindowsXP Pre-SP3-nonIntel-KB953356-x86-ENU.exe
“`
Not big surprise, considering they have shutdown the SHA-1 Windows Update endpoints recently, rendering the update clients for Win2K, XP and Vista useless (and have to use something like WUMT via offline-mode with the WSUSSCN2.cab)
read from this post: https://msfn.org/board/topic/178377-on-decommissioning-of-update-servers-for-2000-xp-and-vista-as-of-july-2019/?do=findComment&comment=1185321
I’m not sure that the claims in that link are factually correct. I know I’ve updated these systems from the live update servers well after the dates in that post. Note that Vista is 2008, and 2008 was supported until January, so a mechanism needed to exist to make it current.
Nonetheless, these update servers can’t run forever due to the high level theme, which is that any security protocols understood by older systems cannot hope to remain secure forever. So either the update servers are available in a very insecure form, and all new updates go through a very different more secure system, or eventually the plug gets pulled. Last year I used WSUS to build an offline store of all of the updates for these OSes so I have an update server and the update catalog in expectation that the live servers will lose compatibility soon.
What is the cutoff for SHA1 vs. newer signatures? I just installed Office 2007 on a machine. Manually installed SP3 (pulled from update catalog, have it on a WSUS update DVD), and Windows Update picked up the rest of the post SP3 updates no problem. SP3 came out in 2011ish.
I could be wrong but I think what they’re doing is pulling SHA-1 downloads from the download center, and this announcement doesn’t affect the update catalog or Windows Update. Since WU is pulling directly from Microsoft servers, the level of security it has is more about TLS than code signing. And nobody has suggested (yet) that executing SHA-1 signed code is about to be problematic, so if there’s a way to get bits to the machine, you’re set.
(Note for context though that there are MD5 signed binaries out there, and many builds of Windows consider it an invalid signature and scream at the user. This seems very strange considering it happily executes unsigned usermode code.)
Looking at the Microsoft Update catalog, there are no longer any downloads dated before May 2017. It looks like any product still under support (mainstream or extended) at that time had hashes updated, so the downloads remain. The date is awfully convenient seeing that Vista exited support in April of 2017. Oddly XP SP3 is still available.
Windows Update didn’t pull any updates for Office 2007 until I manually updated it to SP3. WU used to pull the service pack.
It looks to me like in May/June 2017 they re-signed piles of things so the dates don’t reflect the real date of the update. Taking Office 2007, see how the Compatibility Pack Service Pack 1, 2, and 3 are all listed as May 2017. This even extends to Windows 2000, 7 years after it stopped being supported.
That’s just a problem with the non-IE version of the update catalog. (with wrong dates and such). The IE (activex) version doesn’t exhibit the problem for me. they also have messed their search engine not allowing to find drivers based on the device identificator anymore (again, only happens with the non-IE variant)