So, for my email setup I use an OpenBSD firewall behind a hardware firewall (provided by the telecom), and from there I use OpenVPN to connect up to the VPS that in turn forwards email to my Exchange server.
It works great.
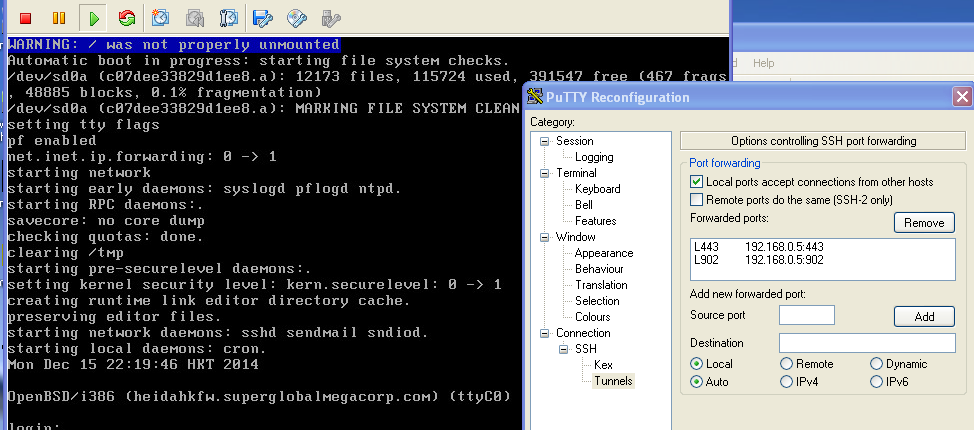
Except that the OpenBSD VM just crashed. And to top it off I had no other way of accessing inwards except for some test machine that luckily was still on, and I had SSH enabled, along with port redirection.
So, a few seconds with putty and you can redirect a local port on your computer to connect to a port on the remote network. Dangerous as hell but, it certainly can save the day! (Yes you can even SSH to a machine, and then OpenVPN to it….)
Checking VMware KB 1012382 details a list of what ports are needed by which versions of their products to do what.
[table]
Product,Port,Protocol,Source,Target,Purpose
ESXi 5.x,443,TCP,VI / vSphere Client, ESXi/ESX Host, VI / vSphere Client to ESXi/ESX Host management connection
ESXi 5.x,902,TCP,vSphere Client, ESXi 5.x vSphere, Client access to virtual machine consoles (MKS)
[/table]
These are the two ports needed for basic checking in on the status of a standalone ESXi machine. So, in this case I can point the VMware fat client to attach to 127.0.0.1 and add in redirects for TCP ports 443 & 902, which let me login, and start a remote console to see how the VMs are doing.
In later versions, you need to use a proper host name. To set this up edit your %windir%\system32\drivers\etc\hosts file, and make sure you have something like this:
127.0.0.1 localhost esxiloop
And then point the client to esxiloop, and it ought to connect.