And let this be a warning to all.
The Data center has null routed because of virus complaints originating from 216.231.130.102.
Sadly I haven’t heard back as far as exactly what this virus is/was and what is going on. Â Just that a ‘complaint’ had been logged against my ip address.
So googling my ipaddress + virus turns up more automation gone awry.
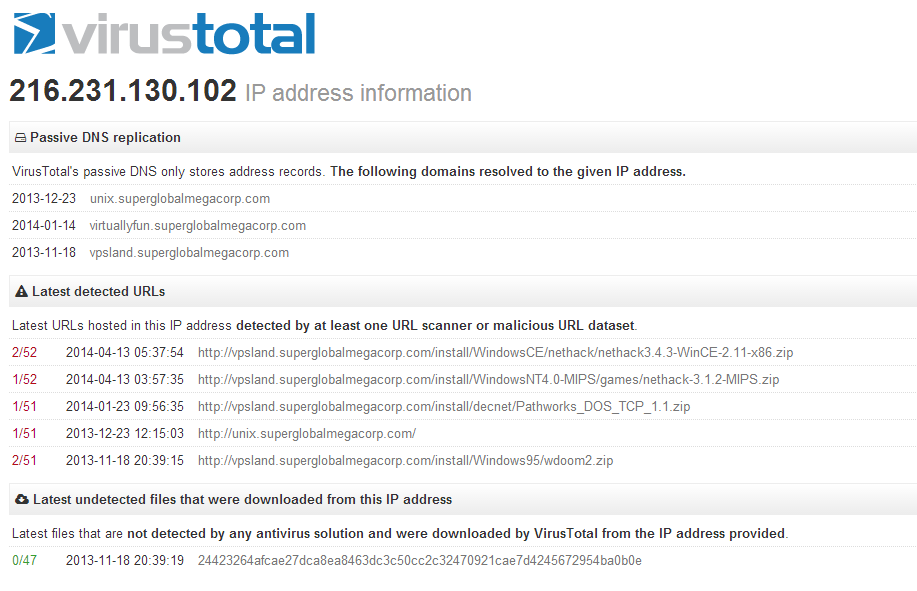
So as you can see this “virus total” is listing a bunch of my  files being infected.  The first thing I noticed is that it’s NetHACK, and for non i386 win32 platforms, both Windows CE for the i386 (it’s not a normal win32 exe), and nethack for the MIPS.
And looking on how they score me 2/52 well these are the sites that now scour around looking for “viruses” and false positives that will get your server blacklisted.
| URL: | http://vpsland.superglobalmegacorp.com/install/WindowsCE/nethack/nethack3.4.3-WinCE-2.11-x86.zip |
| Detection ratio: | 2 / 52 |
| Analysis date: | 2014-04-13 05:37:54 UTC ( 1 day, 17 hours ago ) |
| URL Scanner | Result |
|---|---|
| CLEAN MX | Malicious site |
| Websense ThreatSeeker | Malicious site |
| ADMINUSLabs | Clean site |
| AegisLab WebGuard | Clean site |
| AlienVault | Clean site |
| Antiy-AVL | Clean site |
| AutoShun | Unrated site |
| Avira | Clean site |
| BitDefender | Clean site |
| C-SIRT | Clean site |
| CRDF | Clean site |
| Comodo Site Inspector | Clean site |
| CyberCrime | Clean site |
| Dr.Web | Clean site |
| ESET | Clean site |
| Emsisoft | Clean site |
| Fortinet | Unrated site |
| G-Data | Clean site |
| Google Safebrowsing | Clean site |
| K7AntiVirus | Clean site |
| Kaspersky | Unrated site |
| Malc0de Database | Clean site |
| Malekal | Clean site |
| Malware Domain Blocklist | Clean site |
| MalwareDomainList | Clean site |
| MalwarePatrol | Clean site |
| Malwarebytes hpHosts | Clean site |
| Malwared | Clean site |
| Netcraft | Unrated site |
| Opera | Clean site |
| PalevoTracker | Clean site |
| ParetoLogic | Clean site |
| Phishtank | Clean site |
| Quttera | Clean site |
| SCUMWARE.org | Clean site |
| SecureBrain | Clean site |
| Sophos | Unrated site |
| SpyEyeTracker | Clean site |
| StopBadware | Unrated site |
| Sucuri SiteCheck | Clean site |
| ThreatHive | Clean site |
| URLQuery | Unrated site |
| VX Vault | Clean site |
| WOT | Clean site |
| Webutation | Clean site |
| Wepawet | Unrated site |
| Yandex Safebrowsing | Clean site |
| ZCloudsec | Clean site |
| ZDB Zeus | Clean site |
| ZeusTracker | Clean site |
| malwares.com URL checker | Clean site |
| zvelo | Clean site |
Which now makes hosting any kind of file that some random people with zero accountability can screw up your hosting.
Worse for me, is that my automated backup hadn’t been running frequent enough. Â I’m now suffering through low bandwidth, and replicating all my crap that I’ve acquired through the years on vpsland.superglobalmegacorp.com is just too much. Â And with the possibility of being shut down “just because” is now too much. Â I kind of liked having a dumping ground for old stuff but now that is no longer permissible.
So where to go from here?
I can password lock the site, and require people to contact me for access. Â What a pain. Â I’m sure I could automate it, but I don’t want these arbitrary systems to remove me again so that is out of the question.
I could use some kind of certificate based encryption on everything, and provide a link to the certificate and give instructions on how to use it. Â But obviously this will discourage people who are unfamiliar with the command line, and with OpenSSL (and all the great news it’s had the last week!).
Another option is to use OpenVPN to permit people to access vpsland from within that. Â This removes it from public search, but does allow people to connect in a somewhat easier method. Â And it doesn’t involve something tedious like downloading OpenSSL, getting my servers’s key, downloading the wanted file, decrypting the file, and then decompressing it.
I’ve pulled the latest posts out from google’s cache. Â I’ll try to put up the comments but I can’t promise much there. Â As it stands right now, I haven’t heard back from fragready in over 22 hours, and at this point I want to just get my blog back in operation.
Sorry for the hassle.
–update:
Finally got a response, but not the one I was hoping for.
In situations such as this, where a server has been compromised, we require the server to be reinstalled with a fresh OS installation. Please let us know how you would like to proceed
So basically a false positive on the internet will get your data destroyed. Â Well this sucks.

isn’t there some formal complaint that you could file against this idiotic misguided procedure and get your data back? this is unacceptable.. and if not, couldn’t you host the site on a local machine? of course, bandwidth would be a$$, but no-one could take it down on a whim..
in any case, if all else fails, i for one would be more than happy to log in with a pw/through a vpn or any other alternative. i love this site and would hate to see it go down like this..
I don’t know what to do at the moment. we moved to a bigger place, but went from a synchronous 1GB internet connection (yay hong kong) to a 6MB/.5MB DSL line, as I’m out in the country (still in Hong Kong)..
I would love to host it here, underfoot, but that is going to be out of the question.
Fragready was very cheap for a dedicated box in which I could run my stuff, but seeing that two faceless entities can take me offline, I know I certainly cannot bring the vpsland share public.
I wonder how textfiles & archive.org will manage in this facebook, virial, social media watchdog world where everything *MUST* be for windows..
also, i’m not affiliated with them in any way but i’ve heard that digital ocean don’t put their users through this crap based on some automated false positives, but i can’t confirm it. might be worth a try, though.
I may think about moving, I don’t know. It also means I’ll lose my virtual VAX, and my BBS.. 🙁
What a pain.
we are up now on nodedeploy only because this VM hasn’t timed out on it’s subscription… so I know I need to fix that.
I’m kind of leaning to the vpn solution. Unless I can find some php file downloader, verify you are human thing.
What a giant pain!!!
What about dropping a .htaccesss file into the directory and set AuthName to somethinglike ‘Use VPSLAND as the username and password’? I’d imagine that’d would be enough to thwart pretty much every automated scanning system around.
I may need to do a vpsland2 thing with a redirect so people can see what userid / pass to use…
I may go with this & a VPN which will let people rsync/wget the whole thing.
The idea with the AuthName is the browser should display the on the authentication prompt. I guess if you’re using wget you might not see it. But 403 error could also display the password details.
I don’t know why I didn’t think of a 403. Good point, I can even script it to generate random passwords so it’ll be somewhat usable, and unusable for anyone(thing) that clicks to remember.
It should even work with HTTP 1.0 clients, (like stock NT 4.0) so I can at least download SP6 & IE3.
Good call, now I’m just waiting to see if they format my machine or what.
As bamdad said.
vpn or something would be ok for me too, but I don’t know about the general case.
I was aware of the general false positive problem – our company back home uses Fortinet firewalls and the firewalls subscribe to the Fortinet lookup table – and Fortinet appear to start out with ‘Malicious’ and then rely on their customers to point out the false classification one by one. I very often find innocent sites ‘blocked’ by Fortinet. So I go through a Tor onion proxy to check it, and then I notifiy Fortinet, and they fix their mis-classification and the firewall will let the site through again. What a hassle.
What I didn’t know was that some providers use this to take down sites! Well, lately I’ve started mirroring everything and anything I find on the net, because sites keep disappearing. Bought three more 3TB disks yesterday.. they were on sale and they’re cheap to start with here in Japan.
I keep my own modest site on a Linode server. I don’t know what their policies are in this respect, but as far as the virtual machine is concerned it’s the closest thing to a physical machine you can have. You have to install the OS manually from scratch, set up services (Apache, VPN, whatever) yourself. So maybe they won’t interfere directly.. I’m not sure. But there’s a ‘console’ interface to the system as well so even if it’s off net I should be able to reach it. Linode isn’t the cheapest option but it’s not the most expensive either. And you have to do all the work.. which is fine for my purposes, I only wanted my own machine on a network which has more bandwidth than my home network.
-Tor
I was thinking of getting a iSCSI nas at home for about $8,000 HKD, and filling it with drives.. as I have a single 3TB disk which is almost full already. But with 6MB down it’s not very practical.
It is disheartening to know that faceless organizations can ban your SMTP traffic, but now can report you upstream abuse contacts and have your instance destroyed.
At the time, $50 for a dedicated machine seemed like a good deal… ugh.
OVH has a low-end offering for about the same price: http://www.soyoustart.com/us//us/. Looks like the $49 version is sold out now though : http://www.soyoustart.com/us/offers/sys-e32-1.xml
I’ve used them once before when the low end was still an OVH offering without issue.
There is also their EU hosted Kimsurfi products available too http://www.kimsufi.com/en/.
This looks.. pretty good. I’m going to give fragready a few more hours before I think about canceling but even a 72hour setup isn’t too bad (if they can deliver on that), and in the meantime we ride this VM….
Would vouch for OVH.
Also, fragnet actually really sucks greatly. My 2c.
I liked kimsufi.com’s pricing tiers so I was going to go with them. The problem is that they want to “verify” your identity…. SO like a fool I emailed them my id card & and a bill to show it was me.
I never got a reply.
Such a shame, they did look pretty tempting.
I remember having to do the same thing, though I don’t recall whether I did it via email or a ticket.
they had me email them the details, but I never got a reply… very strange. this seems to be a bad month for me with online services.
Have you tried verbally attacking the fragready people, telling them they’re wrong, you demand to speak to a manager, etc.? Perhaps you can find someone that understands logic.
In terms of ways to do HTTP authentication, I seem to recall in the past that I tried having a page that displayed the required credentials, then redirected to the 403 page, so the credentials (and the explanation for why you need them) is right there on the screen under the dialog box.
Perhaps another option is to put everything inside password-protected .zip files, with the passwords in README files that you’ll see if you do a mass ‘wget’?
well the owner responded to my complaint, but that was forever ago. They haven’t responded to anything I’ve said since. So they are either busy, they don’t know what to do, or don’t care. I know I only account for some $600 revenue a year so I’m not a big player by any stretch.
I’m thinking of doing the 403 thing with having cron generate a new password every 12 hours or so, to prevent some idiotic system from putting me back on their lists.. I also think doing an OpenVPN session to allow people rsync or wget would also be a good thing… I know I wound up losing a bunch of crap, but I still have some 16GB of the site backed up.
In the future what I’ll probably do is get a vps or something with disk space with one provider I can shove backups to, and another sizable hosting system.
I hate that I used to really like fragready, the server was performing just fine, and I really liked that I could mix/match KVM, Qemu, SIMH and various networking methods as I saw fit.
I’m just astonished by their poor customer service (by the owner none the less!) and their kneejerk reaction to some faceless organization that doesn’t like nethack on the MIPS. They didn’t contact me, or anything just null routed my server, no questions asked.
I’m very disappointed.
and those f*ckheads use googlehosted.com so it’s not possible to blackhole them prematurely
it seems some anti-robot download prevention system is a must novadays
Yeah, lesson learned. I think I’ve been using “vpsland” well since I signed up for “vpsland” back in …. 2007..? If not sooner. Although I’ve moved platforms and hosting providers so many times.
But the world of 2014 isn’t the same as 2007 it would seem.
VPN seems reasonable, but you could also do sftp/ftp/http with auth (but don’t do FTP, it sucks)
Whatever it is, tux always said that he really doesn’t like these fly-by-night hosts that don’t give a shit
my only complaint about sftp is that I can’t do it from ancient OS/2 or NT (well Linux, and BSD either)… I’d *LOVE* to do ftp but yeah that’s out of the question.
So I’m going to go with directory auth, and a VPN.
I wonder if a lawyer would write the “virus scanning” company a letter saying that their scan results amount to “slander”?
That sounds like fun, although I could not really justify the 100k it would cost to bring it to conclusion.
blame symantec and trend and whoever the fuck ‘bkav’ are:
https://www.virustotal.com/en/file/7f3cb0113d4d2f2ee98c3eb45fa5b01d93e7ed439d44e5b33579e273888d38f1/analysis/
also Antiy who detects a vncviewer.
https://www.virustotal.com/en/file/a2e57a71b679cccaad92030a6f06b9f3a6f1f5e89737b7ec48e916af9b601d6f/analysis/
LOL WHAT???? You can lose all your data because you have the nerve to keep a copy of vncviewer easily accessible???
HOLY CRAP, this is beyond retarded.
Worse people “trust” these morons.
Trend Housecall uses customer reputation, and shouldn’t be depended on for stuff like this. Symantec detects it as something to be cautious of, not as malicious. Those other guys seem to have seen the other detections and gone OMG–VIRUS!!! — nobody worth their salt depends on results from those other vendors alone.
This makes me think that anyone could contact your ISP and say “My custom Badware scanner says .htaccess is malicious — take them all offline ASAP!” and they’d do it….
I think the worst thing for is that I was never given clear indications of what set them off, or then that four days later and they won’t respond to me at all.
I know my $600 a year wasn’t big $$ to them, but wow. I can’t be the only customer left in annoyance on how they are avoiding people, and arbitrarily shutting down service. Even my open minecraft server got nuked. And I did enjoy that I could easily give it 4GB of ram over there.. .
I very much enjoy your site, and I must say:
In my understanding, your server HAS NOT been compromised.
That means in my opinion that the the rules of handling compromised servers are INAPPLICABLE. Where you go from here I leave to you, but now you might as well contemplate informing their supervisors (some state authority, if any available, or at least “their boss”) of their “nice” behavior.
As a side-note, any chance to get oldlinux up again? 🙂
The owner knows, but they don’t seem to care. Their helpdesk just came up today, although they aren’t seeming to care much about tickets from users…
I’ll probably go with another provider… Either Asia or Europe but closer to home. I hate that up until now they were pretty good, and provided a great service… But now they just don’t care.
Once I figure out where/how this will all end up, I’ll be bringing all my stuff back online.
However if you want oldlinux stuff, I just rsync’d a copy from http://oldlinux.org/, so you can score a copy of whatever you need/want from there…