Well thanks to my latest outage, I’ve gone back from having an Exchange server in the “cloud” (well really a server I rented), to a Virtual Server at home.
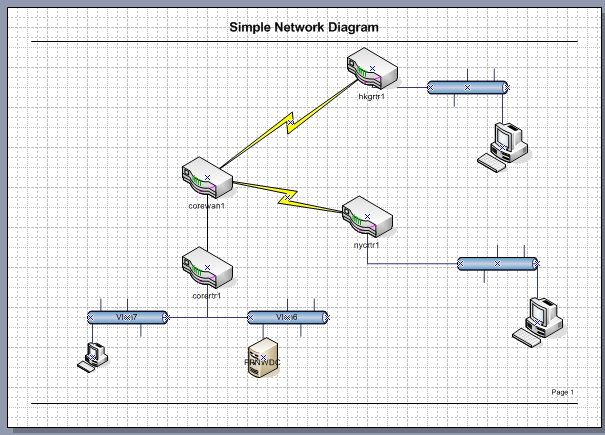
First my ‘plan’ is to get a VPS that I can run OpenVPN on. Â From there I’m going to build a VMÂ at home that will also run OpenVPN, and it will connect to the VPS. Â I will then setup routing, so that the Exchange server can then communicate with the VPS’s internal interface, and the VPS can communicate directly with the exchange server. Â I’ll then configure postfix to store & forward email to the Exchange server. Â This way if the link drops, the VPS will just spool the mail. Â Finally I’ll setup SpamAssasin to filter out the SPAM.
First you will need to have a tun0 interface in your VPS. Â Almost everyone supports this these days so it shouldn’t be too hard… If you cannot get a tun0 interface, perhaps ppp0 with pptp..?
I followed these instructions on setting up OpenVPN on Debian 6. Â Now granted, I’m using Debian 7, but the instructions are pretty much the same. Â Basically you have to setup a CA (Certificate Authority), and then you generate a Server certificate, and a client certificate. Â For my needs, I’m going to issue single certificates for everything(one) that connects into my VPN. Â I also have a network at home that I want routed to the VPS, so this is included (192.168.0.0/24).
A simple server.conf looks like this:
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
dh dh1024.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
client-config-dir ccd
route 192.168.0.0 255.255.255.0
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
verb 3
And a the client configuration I’m using is this:
client
dev tun
proto udp
remote MYHOST MYPORT
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert hong-kong-home.crt
key hong-kong-home.key
ns-cert-type server
comp-lzo
verb 3
In the directory /etc/openvpn/ccd on the server, I have to ensure that I have a file called ‘homefw’ which is the common name of the client certificate. Â It has to contain the following line to ensure that my home network is routed to the VPS.
iroute 192.168.0.0 255.255.255.0
Don’t forget to turn on ip forwarding on both the VPS, and the local ‘tunnel router’. Â For Linux based stuff you need to make sure that “/proc/sys/net/ipv4/ip_forward ” is a 1. Â You can just do a simple “echo 1 > /proc/sys/net/ipv4/ip_forward ” in “/etc/rc.local” or go through your distributions networking documentation to make sure you set it up ‘correctly’.
In OpenBSD I just simply uncomment the following line from /etc/sysctl.conf
net.inet.ip.forwarding=1 # 1=Permit forwarding (routing) of IPv4 packets
If you don’t have routing in place you’ll notice that you can only ping the tunnel interfaces, but not the IP’s on the LAN. Â While this may be fine for a p2p or client setup it isn’t good enough if you want to route traffic.
I’m running VMWare ESXi 5 at home, and thankfully it does support Windows NT 4.0 Server out of the box. Â I setup a Domain Controller running DNS & WINS. Â The VMWare tools won’t work properly with some service pack (4 I think?) but I went all the way to 6, along with the rollup. Â Until you load the service pack, the network adapter will *NOT* work.
I’m going with Exchange 5.5, so again I installed another NT 4.0 server, service packed it, and joined it with the domain controller. Â Remember to install IIS, and the ASP update, as 5.5 OWA needs asp. Be sure to apply the latest service pack for Exchange, SP4 – in the case of Exchange 5.5 .
Now for routing I could go with dynamic routing, or static routing. Â I chose static as I didn’t want to get too involved for this project, as I needed to get email flowing as quickly as possible.
route add 10.8.0.1 mask 255.255.255.255 192.168.0.49 -p
From Windows NT.
It is imperative no matter what version of Exchange you run, that you turn off the open relay “feature”.  A great step by step guide is available here on msexchange.org .
With the basic routing in place you should be able to talk to the Exchange servers’ SMTP engine. Â You may want to setup either a local DNS and populate the VPS’s source address or put in some host entries for it.
# telnet 192.168.0.55 25
Trying 192.168.0.55…
Connected to 192.168.0.55.
Escape character is ‘^]’.
220 exchange.superglobalmegacorp.com ESMTP Server (Microsoft Exchange Internet Mail Service 5.5.2653.13) ready
HELO
250 OK
Now it would be insane to place an Exchange server directly onto the internet. Â Plus when the VPN link is down, it’d be nice to have the VPS store email and forward it when it can. Â So for this task I installed postfix.
For me the big changes in main.cf were:
mydestination = nodedeploy.superglobalmegacorp.com, localhost.superglobalmegacorp.com, , localhost
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 10.8.0.0/24 192.168.0.0/24
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
relay_domains = superglobalmegacorp.com work.com
transport_maps = hash:/etc/postfix/transport
virtual_alias_domains = virtuallyfun.com
virtual_alias_maps = hash:/etc/postfix/virtual
This will permit my exchange server to relay out my VPS, and tell postfix that it’s OK to accept email for the various domains I have.
My transport database is very simple. Â For the email accounts I’m using two domains, so I simply instruct postfix to forward emails destined to these domains to the exchange server
superglobalmegacorp.com smtp:192.168.0.55
work.com smtp:192.168.0.55
And for domains I couldn’t be bothered to create mailboxes for, instead I have their email setup to forward to an existing box using a virtual domain in the ‘virtual’ file.
[email protected] [email protected]
[email protected] [email protected]
Now due to the nature of postfix you need to generate database hashes for it to work, so my script to kick this off is:
postmap hash:/etc/postfix/transport
postmap /etc/postfix/virtual
newaliases
postfix reload
Which isn’t too involved once you get the bits in the right place.
Assuming you’ve got your MX records setup on the outside, with any luck you should start seeing some mail flow through. Â If not telnet to port 25 and start talking to your mail server.
One problem I have is that superglobalmegacorp.com is an old domain, and it’s lapsed a few times to different idiots who not only added to the ridiculous spam lists I’m on, but also spammed from it as well. Â So to deal with SPAM, I went ahead and installed spamassassin, as described in this page.
As mentioned adding the two lines to master.cf got it going
smtp inet n – – – – smtpd -o content_filter=spamassassin -o syslog_name=postfix/submission
spamassassin unix – n n – – pipe
user=spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
And I did change the spamassasin local.cf
use_razor2 1
use_dcc 1
use_pyzor 1
As I do get a lot of spam.
I don’t think most people will care, but this is more so for me keeping my notes straight. Â So yeah I run Exchange 5.5 at home (which I got on ebay for $25!) with Outlook 2003 on Windows XP x64. Â It works well enough for me.