(this is a guest post by Tenox)
A few days ago I wrote a basic packet sniffer / analyzer for Windows for fun. I was working with raw sockets for another application and out of curiosity winged a small packet sniffer in just 200 lines of code. I actually used it already several times to resolve some firewall port blocking issues, instead of spinning up Wireshark, so I decided to release it to public.
The good:
- Portable, a single, tiny exe
- Easy to use
- Doesn’t install any driver like libpcap
- Extensible, just 200 lines of simple code
The bad:
- It’s very basic and doesn’t allow anything outside of simple unicast TCP, UDP and ICMP, most importantly layer 2, broadcasts, multicasts, etc are out of question
- Currently it doesn’t directly support filtering, however you can just pipe it to findstr to filter for anything you want
Raw socket limitations are possibly the biggest issue, but if you just want to find out simple stuff like traffic going to a given port or ip address it’s a perfect little handy dandy tool to carry around.
To use snoopy you specific IP address of the interface on which you want to listen:
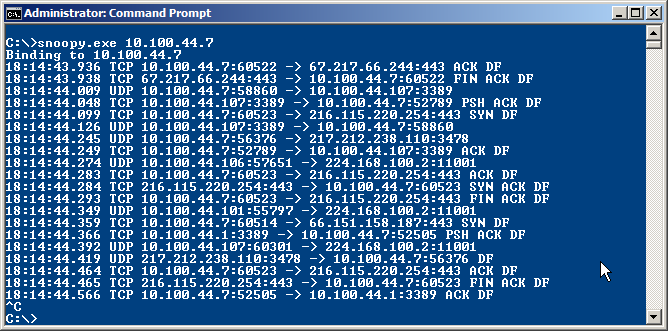 There also is a verbose mode which shows some more detailed protocol information:
There also is a verbose mode which shows some more detailed protocol information:
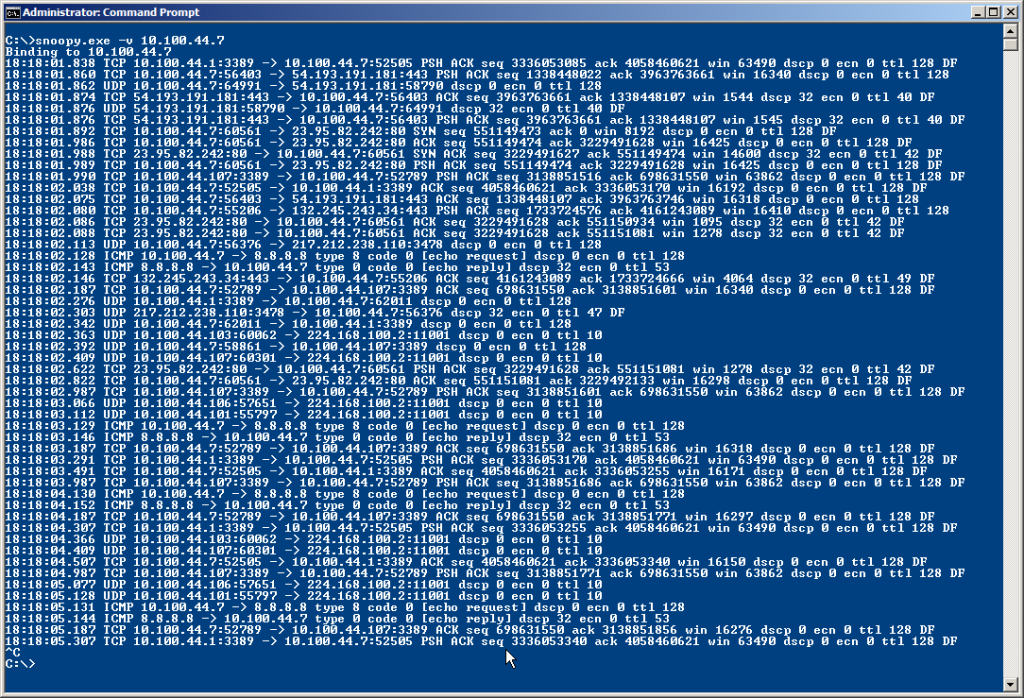 Today I decode ICMP message types, TCP flags, sequence, ack and window numbers and DSCP, ECN, TTL and Dont Fragment flags for IP. I’m thinking of embedding /etc/protocols and /etc/services in a .h file to resolve them on the fly.
Today I decode ICMP message types, TCP flags, sequence, ack and window numbers and DSCP, ECN, TTL and Dont Fragment flags for IP. I’m thinking of embedding /etc/protocols and /etc/services in a .h file to resolve them on the fly.
Bug reports and suggestions most welcome!
Available here: http://www.tenox.net/out#snoopy
